SANS Holiday Hack Challenge 2020 Write-Up Part 2/2


Hey Everyone! Glad You're Still Here Cracking At The SANS Holiday Hack Challenge AKA KRINGLE CON 3 (2020)!
If y’all missed part one you can just reverse reverse! Clicking here : https://www.jameskainth.com/cyber/2021/01/11/HolidayHackChallenge2020.html
At this point we’re 2 almost 3 Christmas trees in, so the challenges aren’t necessarily crazy hard but they’re gonna go from 0 to 100 real quick it feels like. Hahaha no worries that’s part of the fun ain’t it! Love a good challenge! Hack On!
Objective 5: Open HID Lock
- So at this point you’re given a proxmark (HEY THAT SOUNDS FAMILIAR! Josh Wright I hope you got yours as well!)
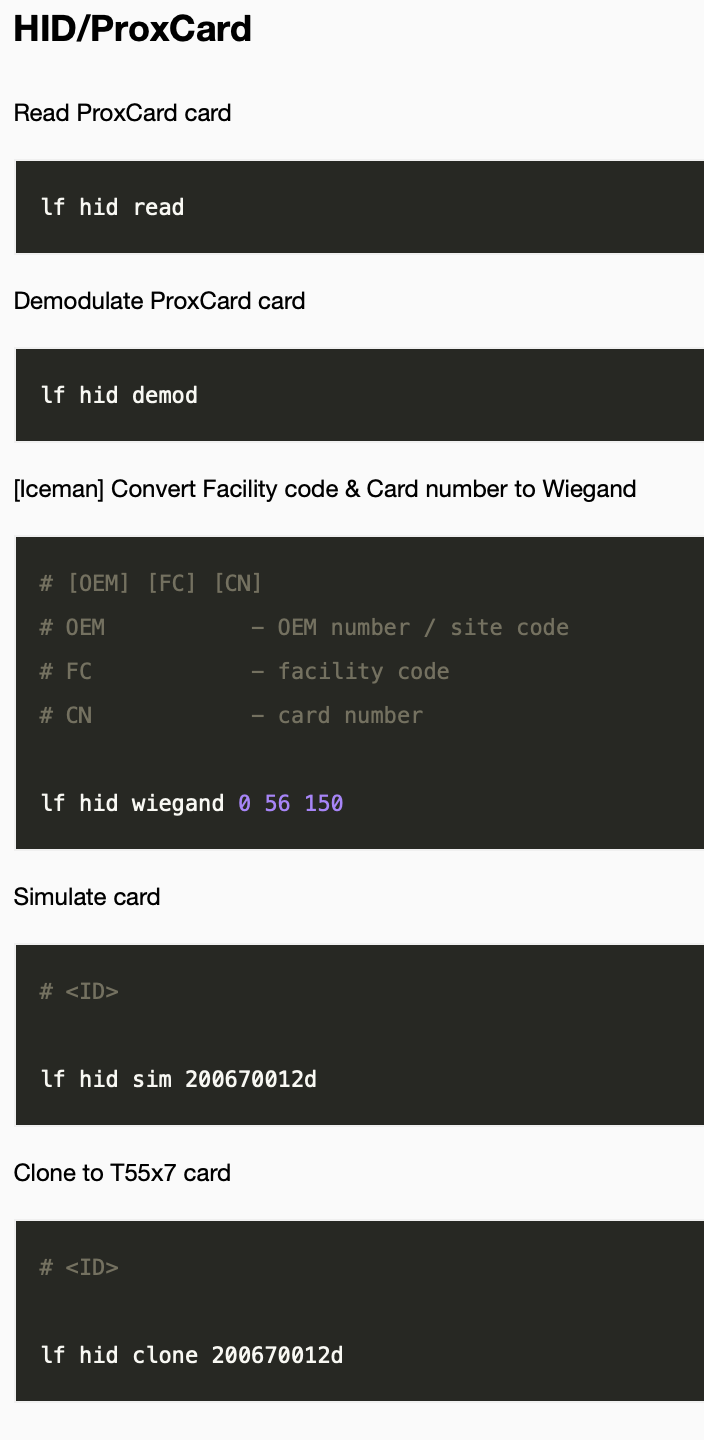
- Googling how to use it, the syntax is pretty ez, there seems to be a read and then a sim for simulate which makes sense. Here’s a nifty cheat sheet https://tagbase.ksec.co.uk/resources/proxmark3-cheatsheet/ Scroll down to where it says “HID/ProxCard” and you’ll get a taste of the commands we gotta use.
-
Ok, so it looks like
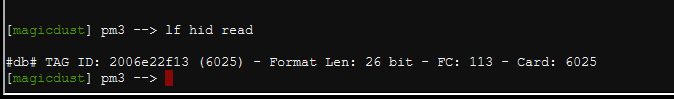
lf hid readandlf hid simare gonna be our best bet. The question is whose ID do we have to clone/simulate? -
Asking around, we figure out that the person with access is actually an elf called Shinny Upatree. Someone we recognize from a challenge earlier with the S3 buckets.
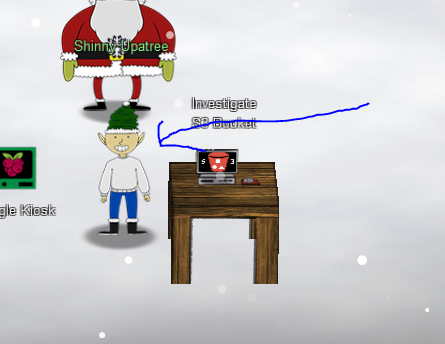
- To do so, we use “lf hid read” to get the RFID parameters we need to simulate. and it’s as simple as using “lf hid sim” to then clone it. Shockingly easy, some may say :grimacing:.

- Once you get into the locked room in the workshop, it’s a dark room that’s like a maze that you navigate to the glowing dots to exit on the other end.
- PLOT TWIST!! You end up BECOMING SANTA!! (Pardon me already being Santa in the image above…this is my first write up and I made the amateur mistake of not taking enough screenshots and documenting what I did, which isn’t my level of preference for a writeup, also why I didn’t submit the writeup :rofl: but hey it’s my first so, live and learn. God do I know it… live and learn)

- Also shoutout to the folks who made the challenge, I gotta show the narrative that’s going on with the challenges as well, it’s hilarious and very fun!
Objective 6: Splunk Challenge

- Coolio let’s go get it!
- I used to work in a SoC so I know the command syntax, but if you ask the elves for hints they’ll tell you to run the command in the search bar
| tstats count where index=* by index, basically count them all except the sub-techniques (not all is in the image you’d have to run the search yourself :wink: )
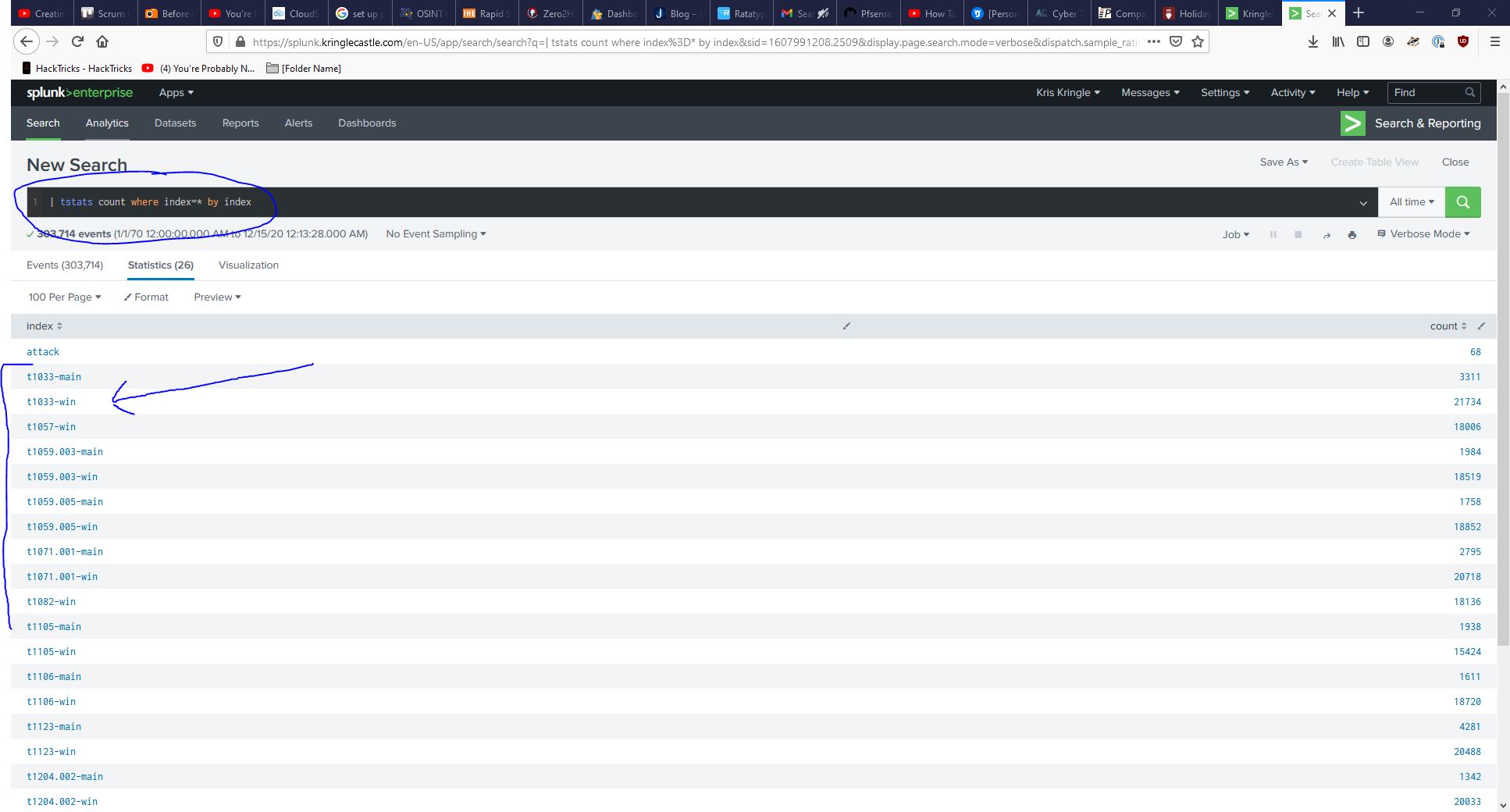
- Count 13 there ya go (unless you just brute forced it lol, that works too)

- For the next question you can run the same search and use logic with reference to the MITRE ATT&CK Framework.
- Moving forward with the ‘training questions’

- Ok I feel like I copped out on this one. I’m a DFIR guy (I don’t even feel like I’m competent enough to call myself that yet :sweat_smile: ), I know RegistryKey Values, HELL I have the DFIR Training’s Site list bookmarked. Check It Out! here … https://www.dfir.training/resources/downloads/windows-registry which is by no means as exhaustive as it looks either (thanks Windows :joy:).

- “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography” Type her in and there you have it!
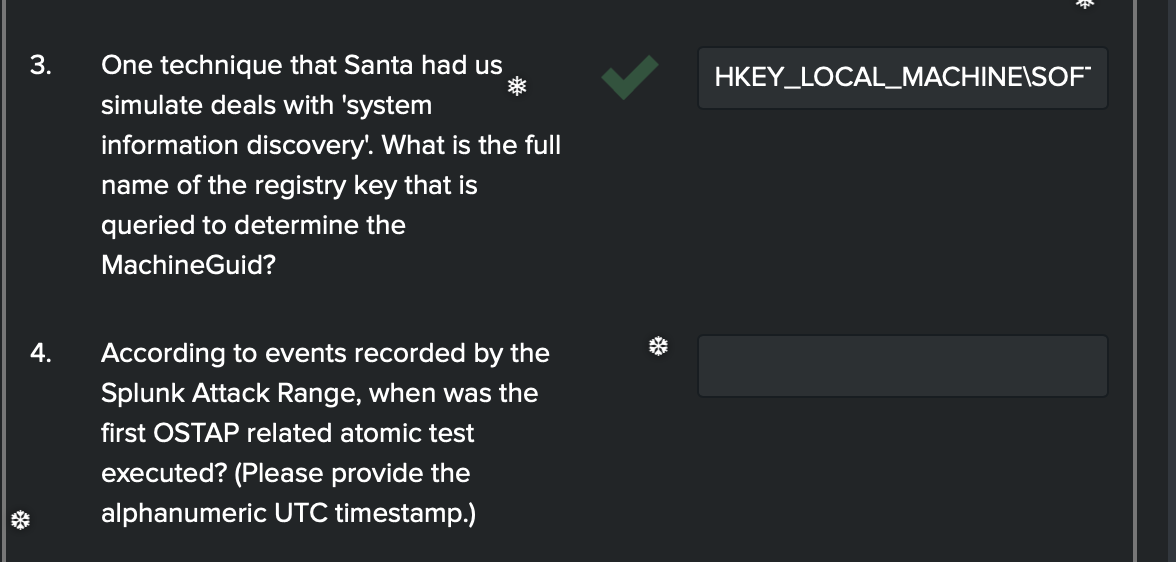
- Hmmm ok, OSTAP so let’s sort by time as well and make sure we get the right one.

- It’s already in UTC so les type that in.
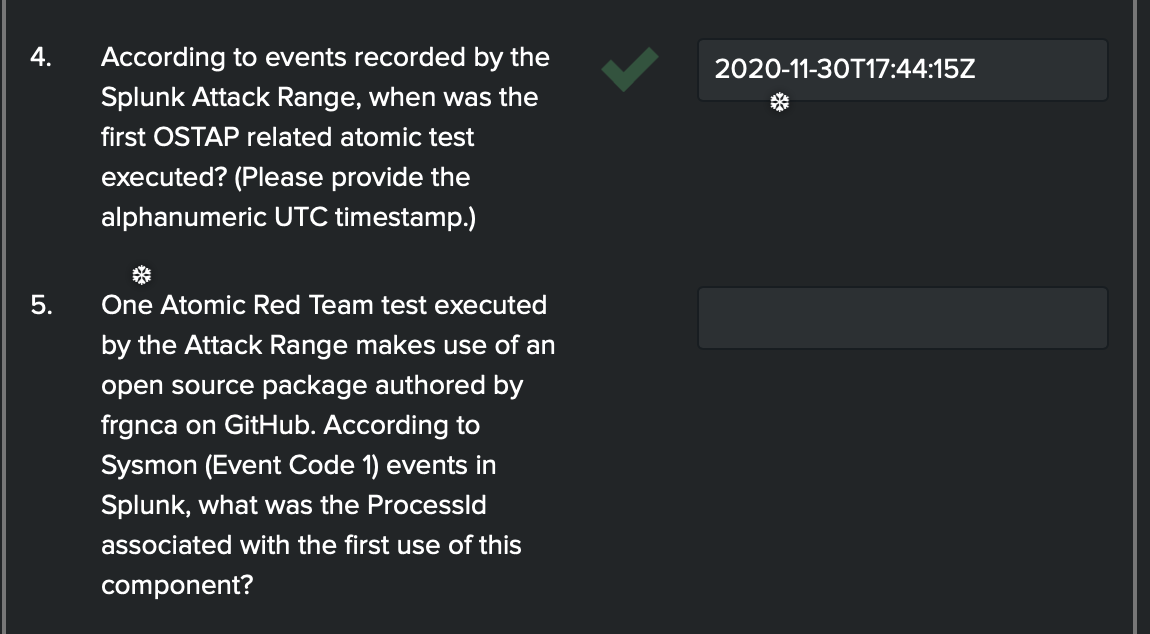
-
:fire: LIT Les keep goin!
-
Ok, so now we gotta do some research and googling for this open source package, but hey they were nice enough to tell us it’s by someone named “frgnca” … a nice 2 min search later and we find this repo which is useful :smirk:.
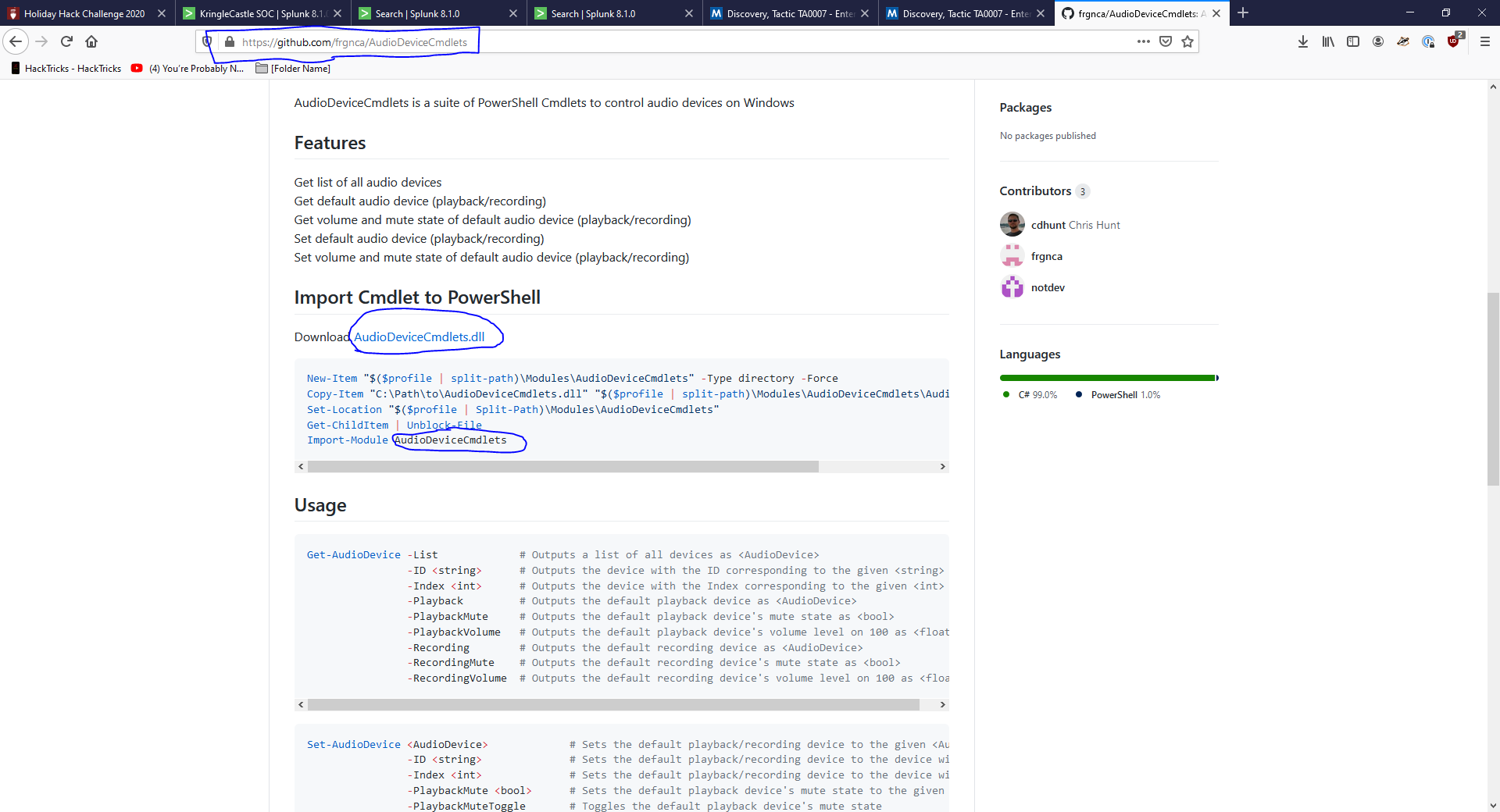
- Hmmm so let’s go SPLUNKing for “Window Audio Device” since it uses the Audio Device cmdlet.
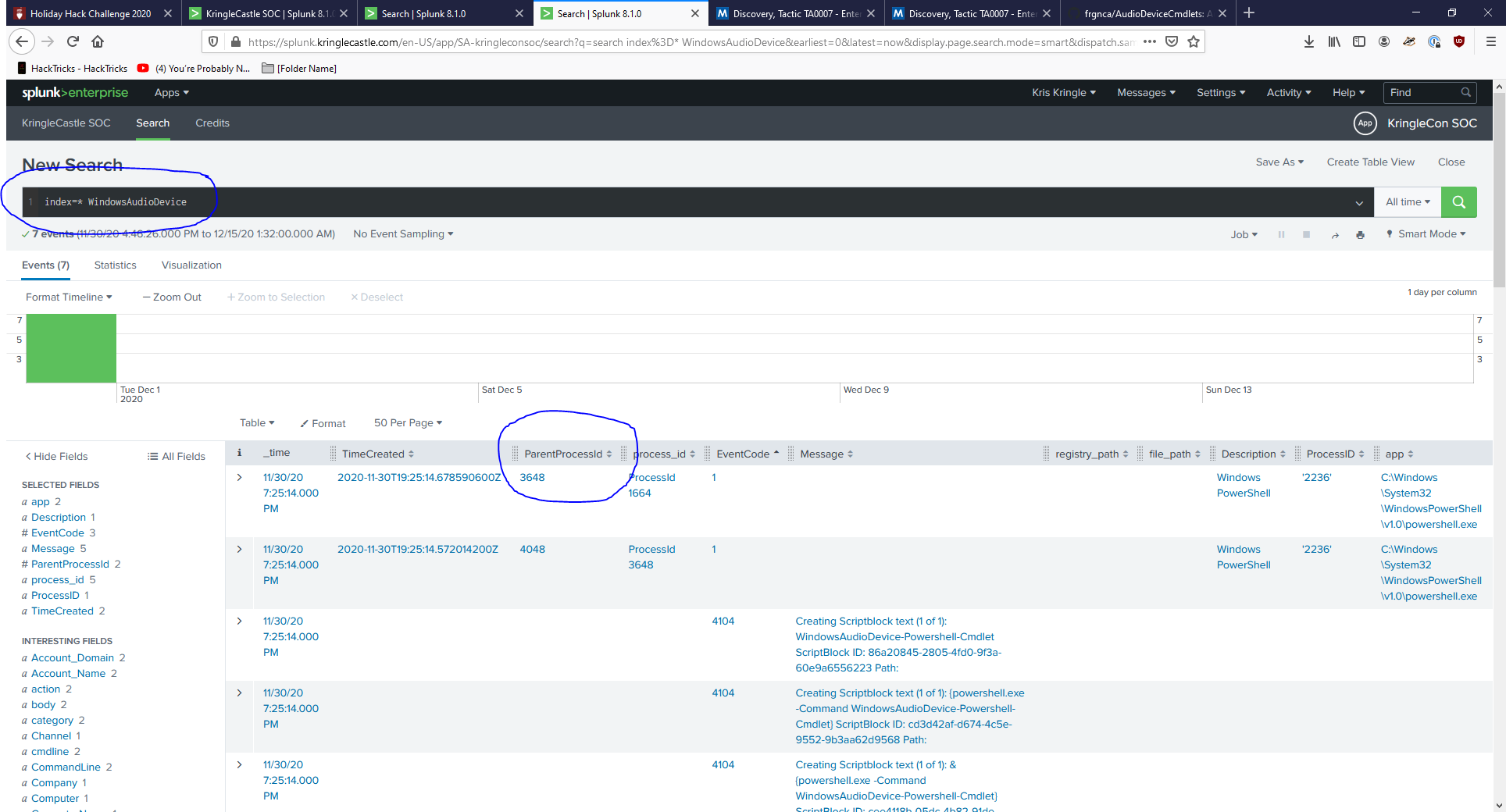
- Aight we are rockin and rollin, let’s make sure we get the time right as well. Let’s try PID 3648.
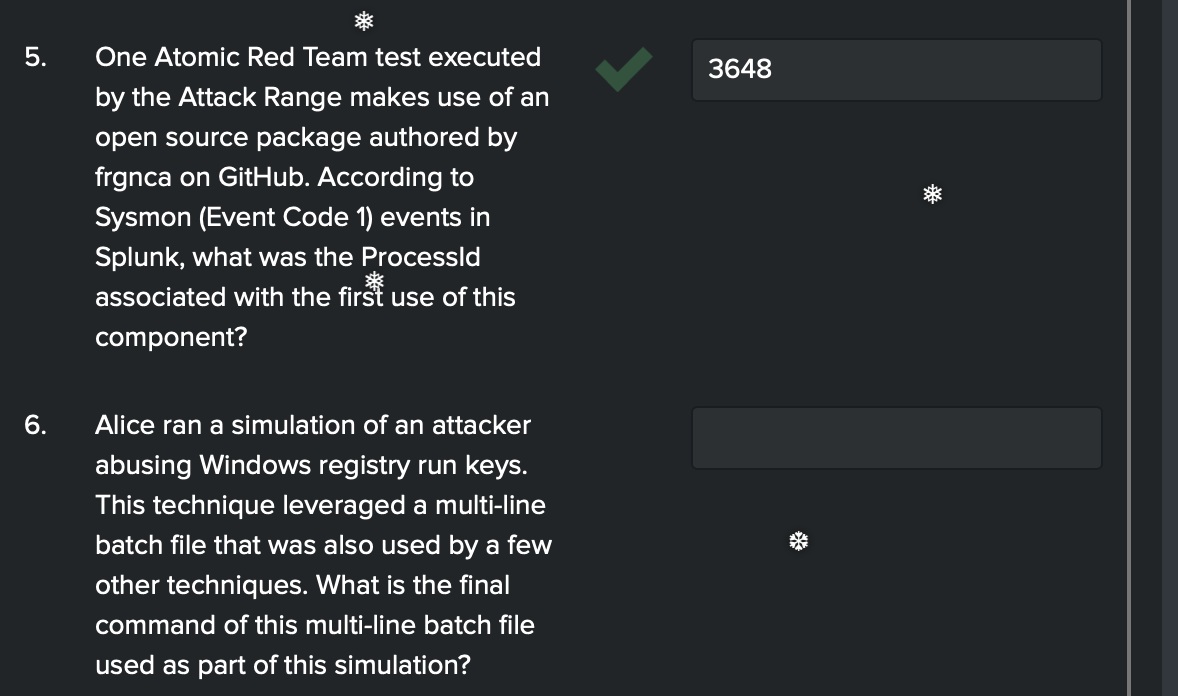
-
YESSS LES GO GET SOME MORE BREAD!!!
-
OK, so we gotta keep exploring the Atomic Red Team Repository, sounds good to me! I just wanted to take a note, when I was in college I discovered this repo and was hella intimidated, but now I’m perusing around and working through it with the SANS Holiday Hack Challenge so, hooray, look at us go! If I can do it, YOU CAN to!
-
The question asks for a batch file, so let’s look in the repo for what they have.
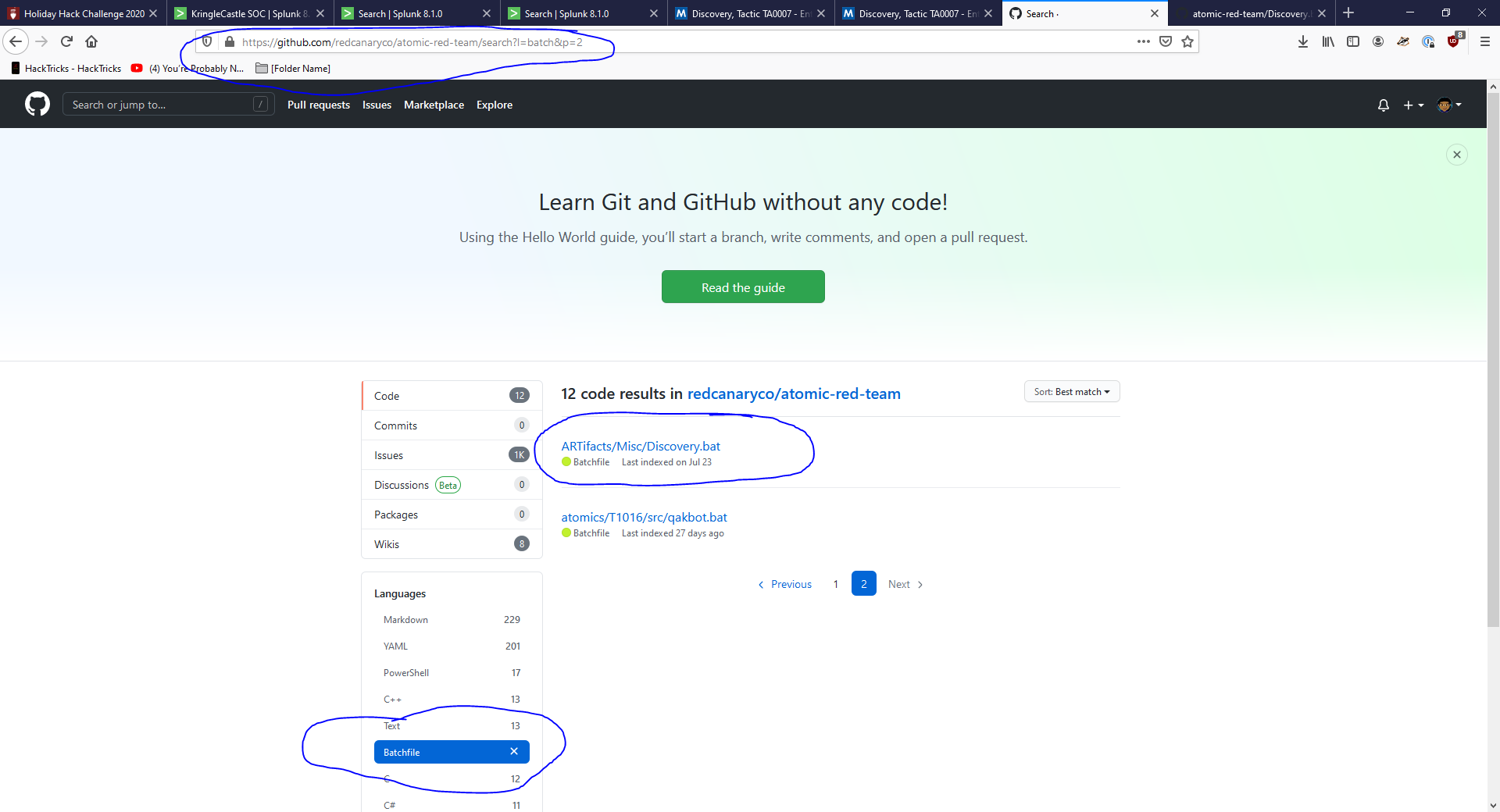
-
Ok let’s try the top one (luck says I’m right with that lol).
-
Scroll Scroll Scroll get to the end what does the question want?
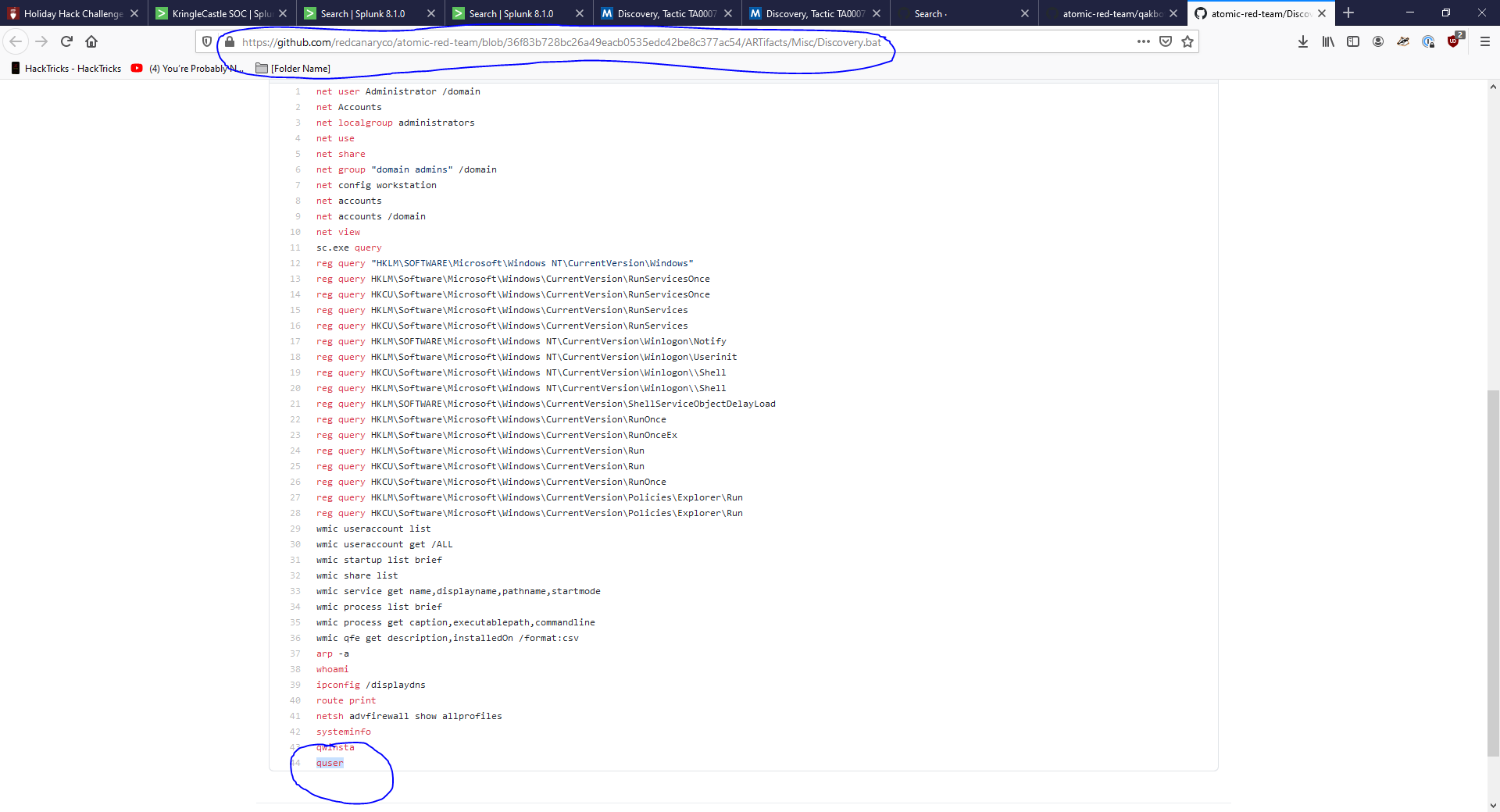
- Let’s try it!
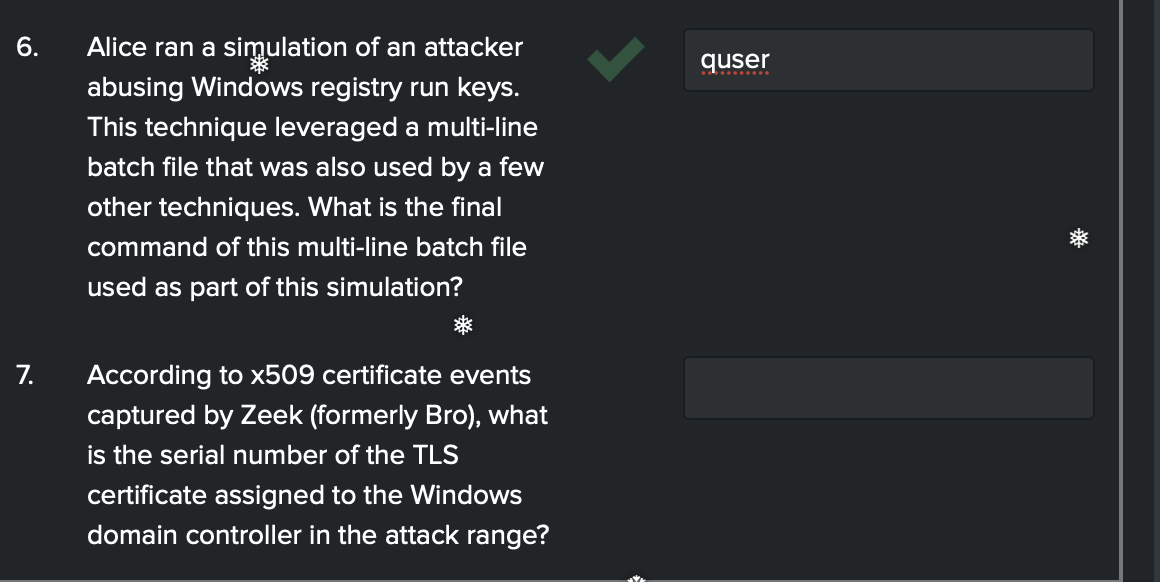
-
Rock and Roll! Let’s get to the Splunk Documentation to see what they’re talking about with this certificate field.
-
Google Google Google really I swear Excel-fu and Google-fu is STRONG in the DFIR community :joy: among having real kung-fu/martial arts ninja skillz, fencing, or being a champion powerlifter! Some of us aren’t just good with computers folks!! :wink: KEEP ON KILLING IT OUT THERE YOU INSPIRATIONS! You Know Who You Are, and I aspire to be like y’all! Skillzz in all the things!
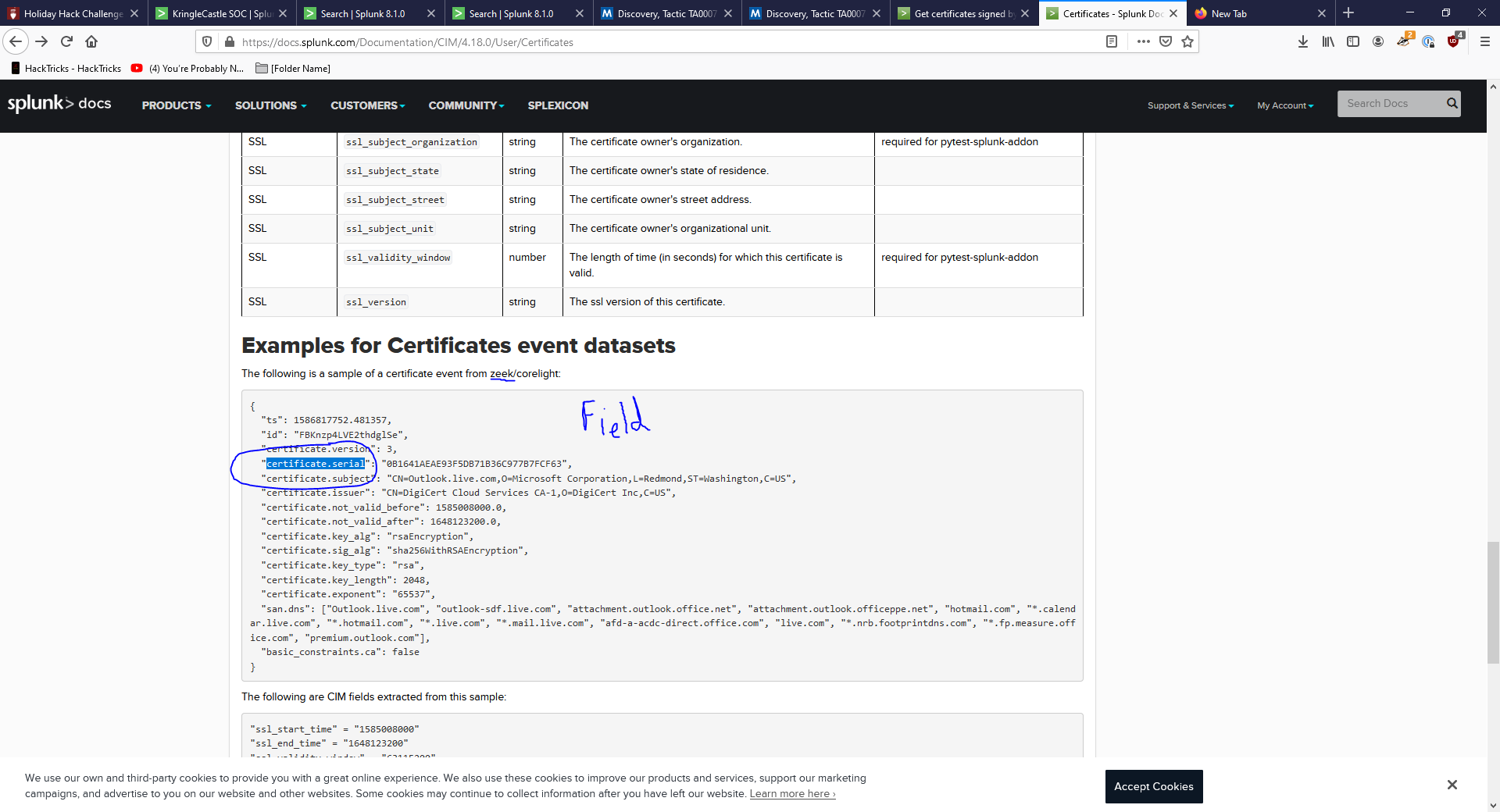
- Ok so this seems useful…again LES GO SPLUNKing!
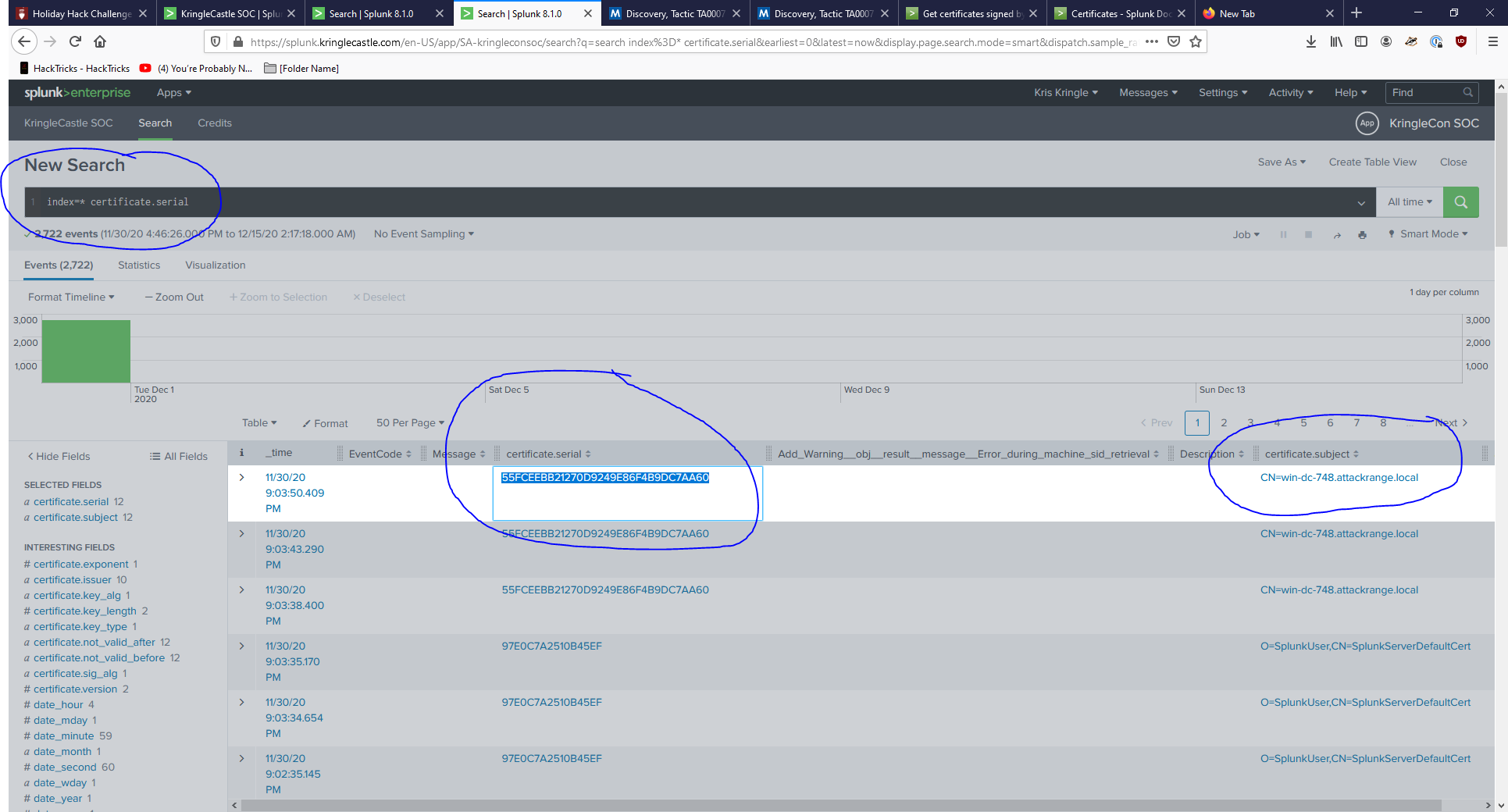
- This is promising…cp that suckah in and SCHWEET we’re in business! Oh wait SO THESE WEREN’T Training questions, we needed to do them to get a secret from Alice! What’d she say? Watch a talk!?
- WELL I’D LOVE TO! I think you should too :smile:
- OH MAN I LOVE THESE PEEPS!!

- I barely even know most of the DFIR community but I feel like they’re family. That’s hilarious!

-
Ok les do some Crypto!
-
Hold Up, HOW DO THEY KNOW I have a really annoying requirement of reading RFCs to learn! An old protocol??? Les do that Googling.
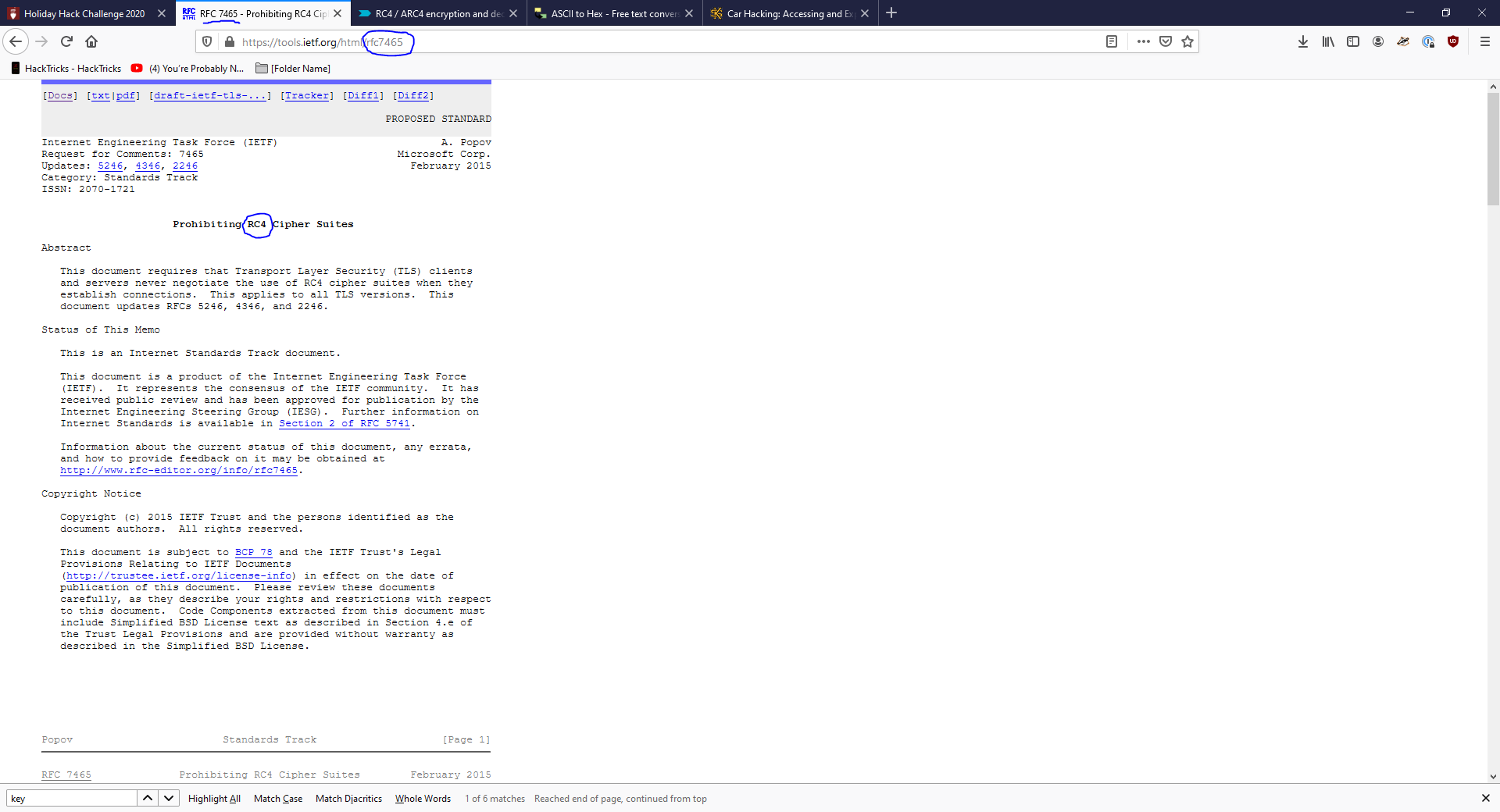
- AIGHT Looks like we be leveraging RC4 Crypto



- “The Lollipop Guild” sounds cute.
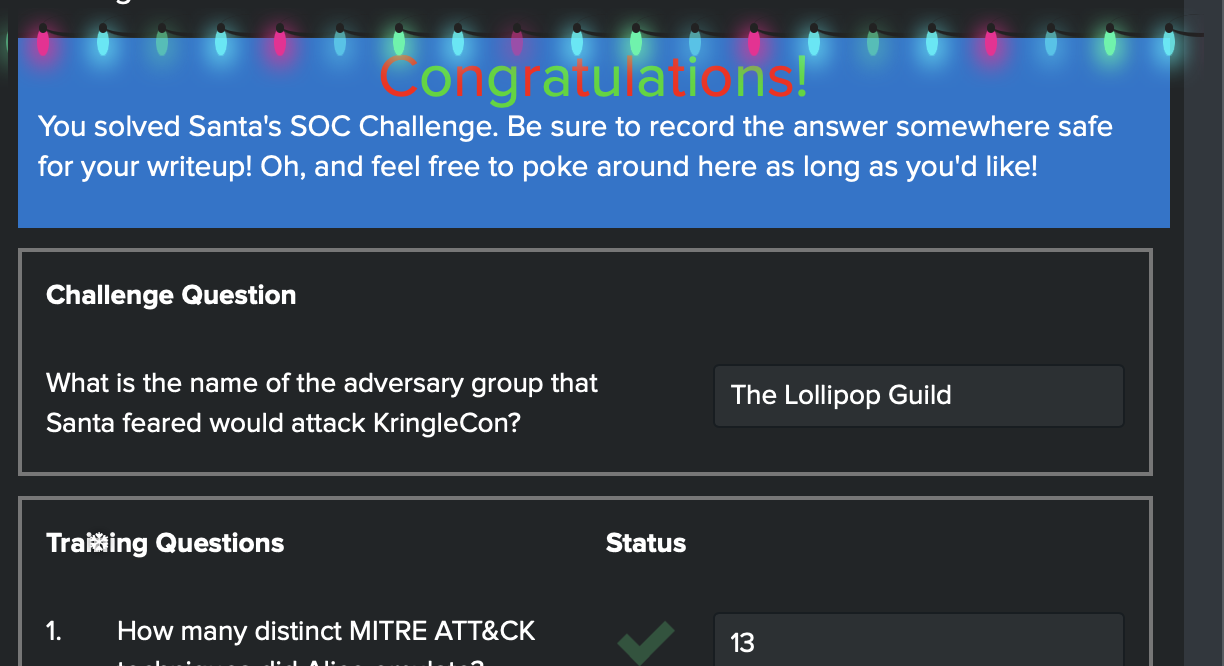
Objective 7: Solve the Sleigh's CAN-D-BUS Problem
-
Car Hacking….ok….ok…calm down James….this exciting yes….don’t go breaking your Subaru just yet
-
Seriously if you haven’t watched any of the talks yet. Shame on you!
-
If you go to the sleigh it asks for you to identify the unlock code from the sleigh, but you have to figure out what that code is first…
-
So it basically looks like it’s just messing around with Hex and trying to sort out the noise. Seems easy enough, just tedious and might take awhile. This is the part of the challenge where I started to make friends in the Discord who helped to work with me to figure out and track the hex value to the controls…. I wish I had taken better notes but I didn’t… Again I’m sorry. This is my first Write-Up I can’t go from 0 to John Hammond as quickly as I wish to be.
-
Here’s a gif basically identifying the malicious hex tho and removing it. I DID DO THAT!! I made a gif, so I’m trying I promise! You live and ya learn!
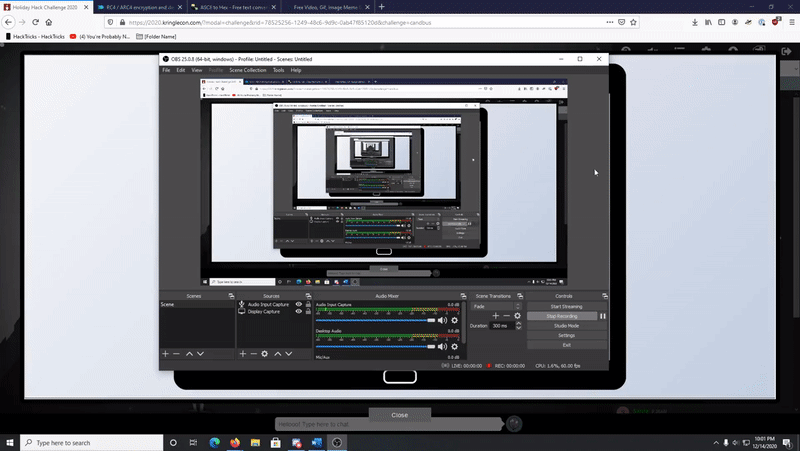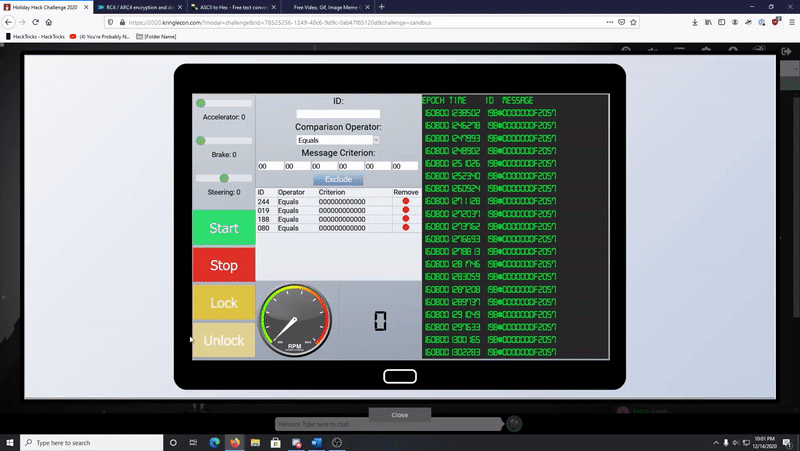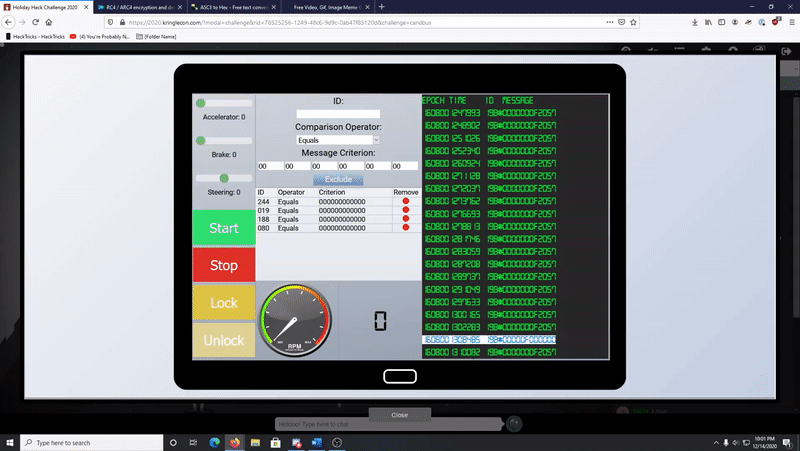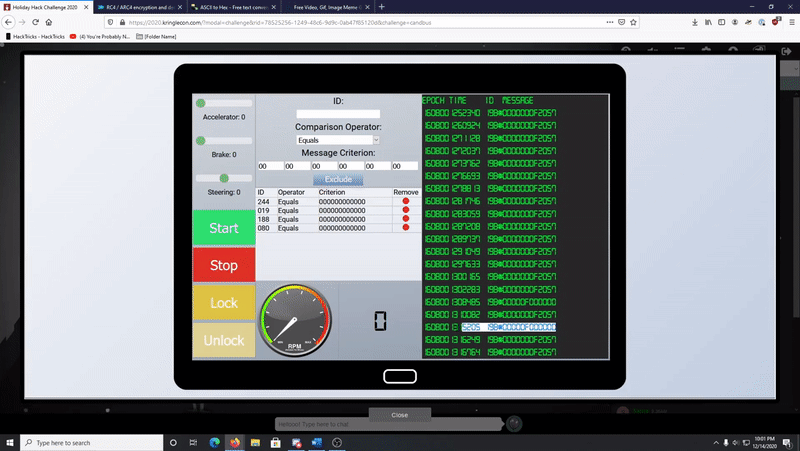
-
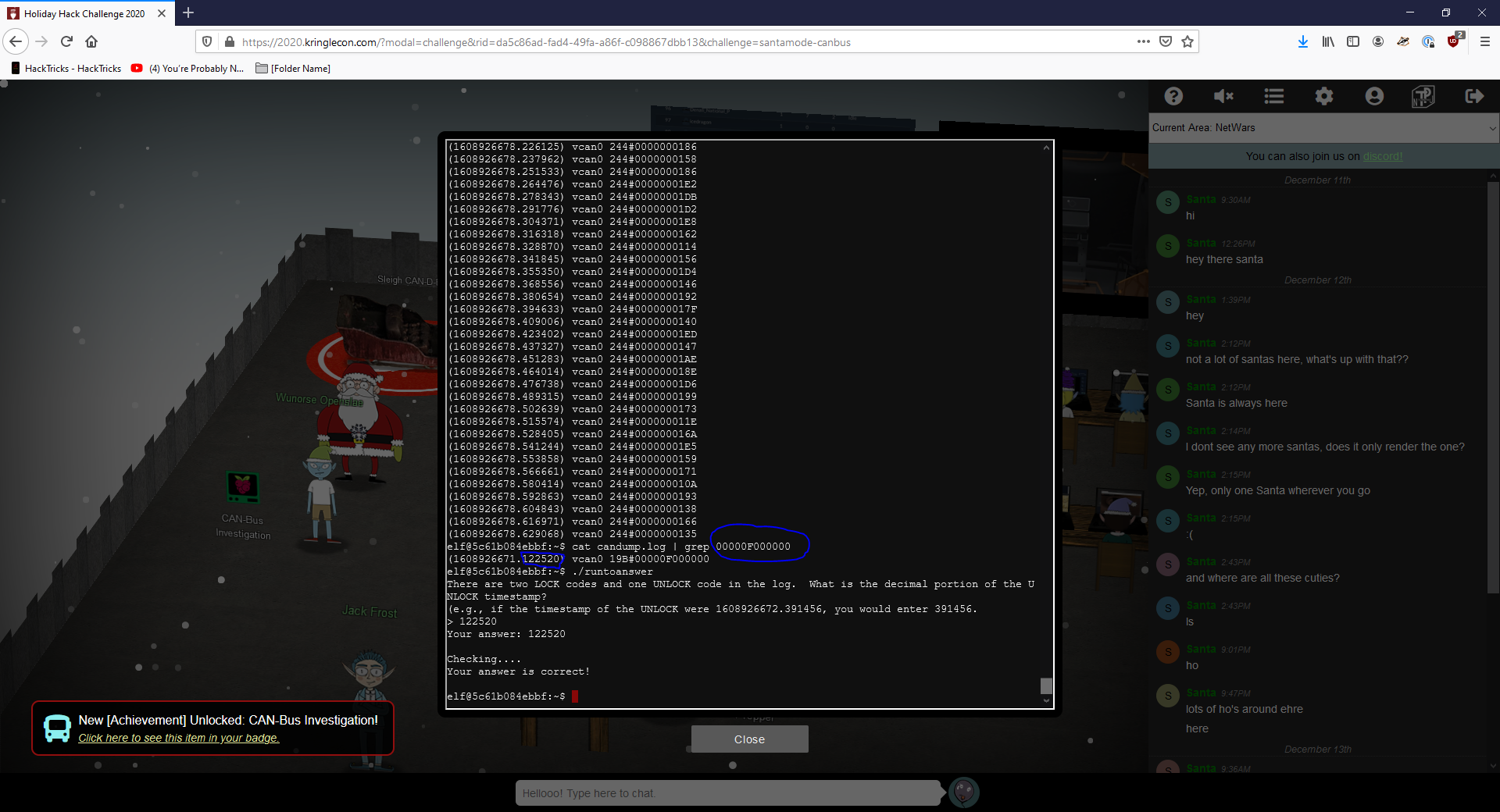
Looking closely (the gif could’ve been better too…live and learn) you can see the unlock code is 0s F and 0s
-
Working on the Sleigh terminal with some linux fu, you can grep that to solve the challenge.
Objective 8: Broken Tag Generator
- OKIE let’s try it! I feel like I’m out of my depth, and I’m flying by the skin of my teeth with four Christmas trees but, I’ve learnt so much already and I’m LOVING IT! I love the hustle a DFIR/Cyber Pro needs to have. That’s why I love my job, and I love the industry! We support each other!
-
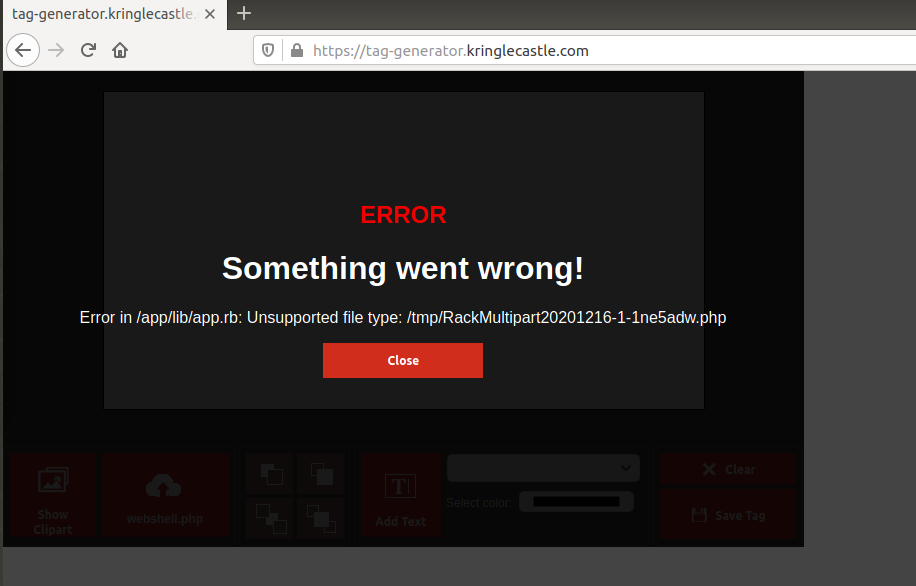
So the tag generator is broken and we gotta fix it, cool. I see a php extension, that could come in handy too.
-
It’s a WebApp so my PurpleTeam-Senses tell me I’m gonna need to BURP! No not that burp, c’mon! I maybe a n3rd but I have some class! Just ask my friends! I wore suits, and ties all the time in college…except for that halloween I was in the news for wearing a Pikachu costume :thinking: .
-
You can upload your own files, so you could probably upload a backdoored file with a php exploit… I spent a few hours tryna do that but never got it to work. Some other folks did, so I’m looking forward to reading their writeup. Perhaps one of the SANS selected winners were able to get it, they’re more skilled then me at this point, but I’m getting there! :smile: CONGRATULATIONS TO ALL WINNERS too btw! :tada: hopefully by the time the next challenge comes around I’ll be able to have a shot at a free SANS course!

-
So there’s some parameters there in relation to the uploaded file, also looks like there’s some directory traversal possibilities in this webapp too. Classic
OWASP Top 10amiright friends!! :grin: I’m curious what’s in that file, so I gotta get to that app.rb file :thinking: -
Doing some research, I was able to determine the webapp is vulnerable to LFI (Local File Inclusion) here’s a post by Acunetix that details it in relation to Directory Traversal that we’re gonna try.
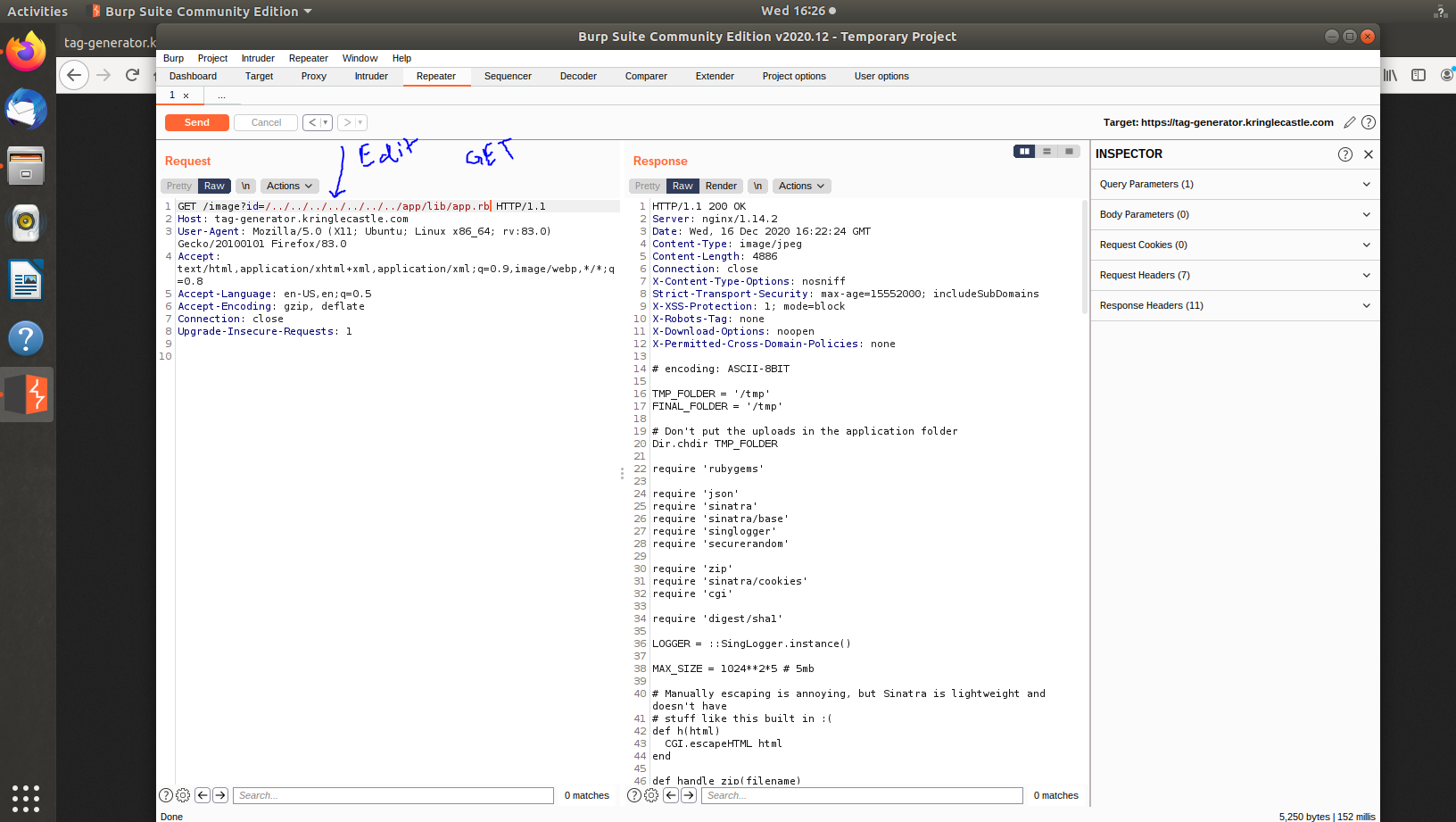
- OOOOO ok now we’re getting somewhere… something about Frank Sinatra? Maybe knowing that could come in handy (Sinatra specifically lol…. I should chill on the Jamesisms for second here. Let’s look closer)
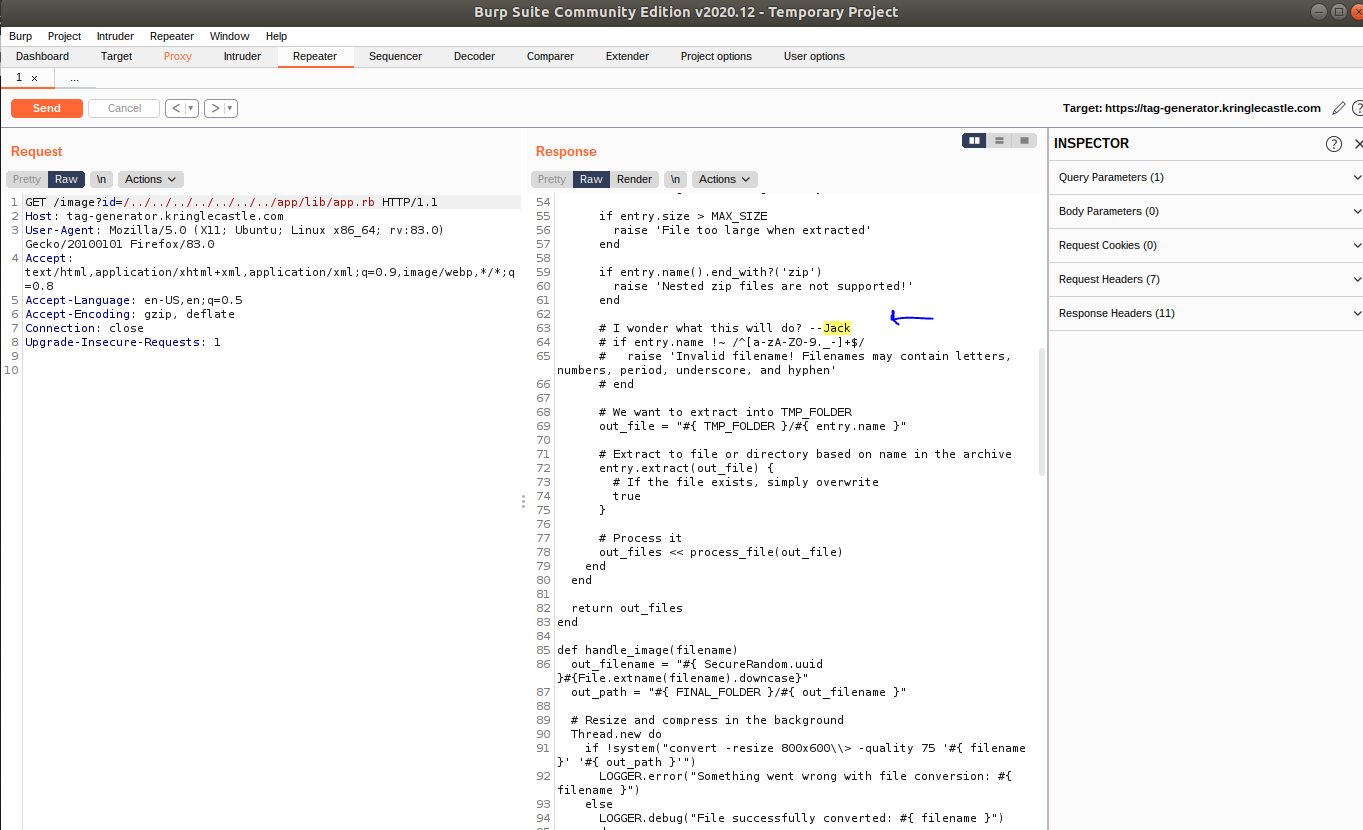
- GAHHH THAT RASCAL JACK FROST!! This is Santa Claus 3 ALL OVER AGAIN with a mix of 2 because seems like there’s a robo Santa too :rofl:
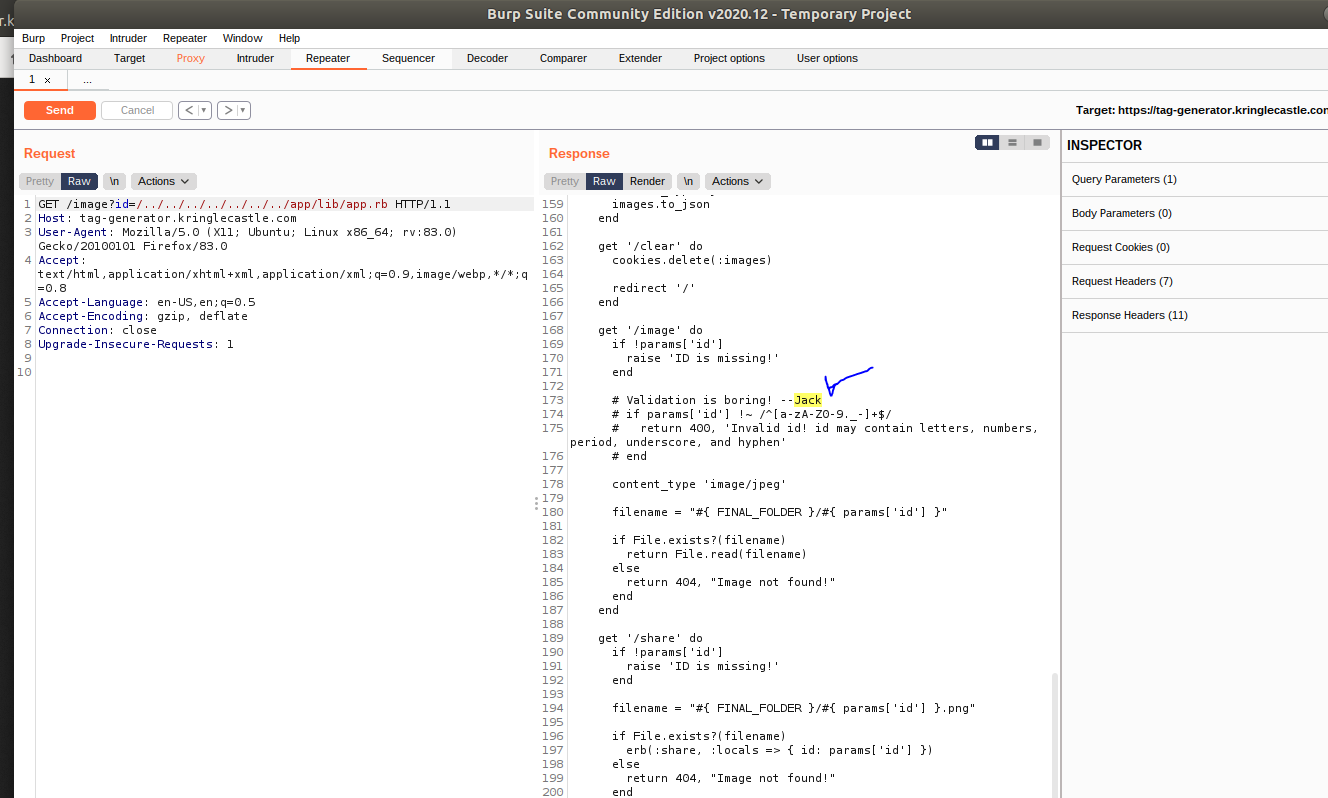
-
VALIDATION IS BORING!?! Ok so laziness is a good thing sometimes…it’s what makes us automate all the things! BUT HERE it’s a BAD THING….WHEN IT COMES TO SECURITY DON’T BE LAZY…I REPEAT…WHEN IT COMES TO SECURITY DON’T BE LAZY!
-
So looks like we can traverse through and ls for the environmental variable we’re looking for ‘GREETZ’
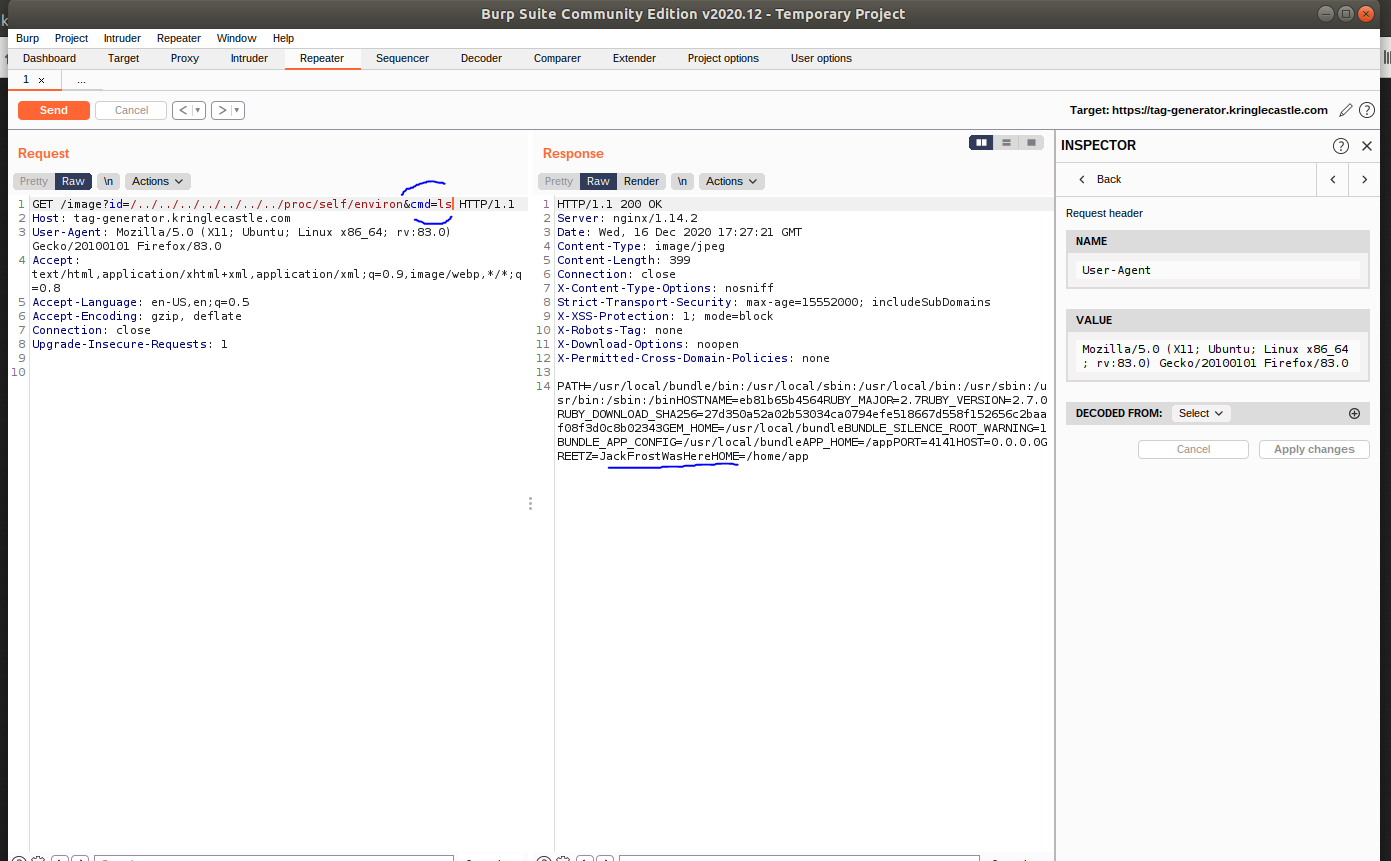
-
Jack Frost you sneak!
-
Ok folks, it’s at this point where The Holiday’s kicked in for me and my family was screaming for me to get off the computer and spend time with them. I also wasn’t certain how to continue on with the next challenge. I know I have to use Scapy, and do some DNS spoofing, among more fun things! Unfortunately, I don’t know how to do that without some heavy research, that I just didn’t have the time to do. BUT I’m sure someone else knows more than me, to which I’ll post a link here to their write up when this post goes public
-
Here’s the next challenge I gotta start learning SCAPY for!