Dissecting Packets On The Byte Level
Yo Wuddup Everybody It’s Ya Boi James here coming at you with a new blog post!
We’re gonna talk about three types of packets that encompass the main functions of computer networking, the reasoning behind this is for y’all to understand packet captures and general networking in more depths. What we’re getting into now is the granular bit of computer networking and that’s on the byte heck bit level. So we’re going real down and dirty in the weeds here, and that’s why I think it’s so important for y’all to get this exp and understand it.
So let’s get into it
If y’all don’t remember the protocols I mentioned from our previous videos I’ll give y’all some context about them before we break them down
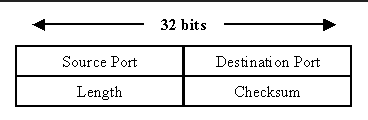
UDP: User packet Protocol RFC 768
- requires no verification that a message has been received
- does not leverage the 3 Way Handshake TCP does (SYN SYN-ACK ACK)
- No flow control or error recovery
With the above list in mind it makes sense as to why the UDP packet is small and simple.
- Source and Destination Port Field so the packet knows the endpoints of the connection (16 bits each for Source and Destination- totalling in 32 bits)
- Length Field details the length of the packet header and data (16 bits)
-
Checksum Field which is optional is like verifying a hash, it verifies the integrity of the header, if it’s damaged or has been altered in transit (16 bits)
- With that the UDP Packet Header totals 64 bits
As a result of the above, UDP is known as a connectionless(because it doesn’t wait for a connection, it just yeets the data) and unreliable protocol, so it’s used in situations where TCP would be too slow or too complex. With that in mind, it makes sense than why UDP is the transport protocol of choice for DNS (Domain Name System, Runs On Port 53), SNMP (Simple Network Management Protocol, Runs on 161/162), and TFTP (Trivial File Transfer Protocol, Runs on Port 69). There’s many other application-layer protocols that use UDP as their transport-layer protocol, but sometimes you might need more control over your data, which leads us to TCP.
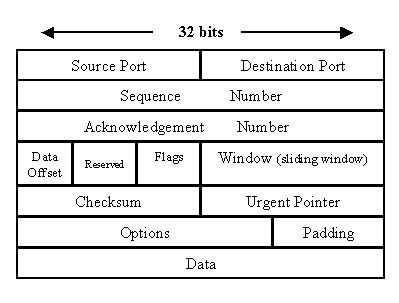
TCP: Transmission Control Protocol RFC 793
- Connection oriented providing full duplex point to point connections
- Leverages the TCP 3 Way Handshake (SYN SYN-ACK ACK)
- Supports multiple upper layer conversations as TCP data is organized in “Streams”(streams of bytes) *Provides reliable delivery as sequence numbers are used to organize the data being sent, as well as the order, so if a TCP stream gets out of order, TCP will retransmit it in the correct order.
- Has network adaptation and flow control allowing for data to “buffer” so as to manage fast senders and slow receivers adapting to the network as needed to maximize throughput without overloading the network.
- TCP monitors the exchange of packets to estimate when an acknowledgement should be received and if the time estimated is exceeded TCP will automatically retransmit.
- Source and Destination Port Field so the packet knows the endpoints of the connection (16 bits each for Source and Destination- totalling in 32 bits)
- Sequence Number is the number assigned to the first byte of data in the current data stream. It can also be leveraged to determine an initial sequence number for an upcoming transmission. (32 bits)
- Acknowledgement Number field is the number of the next sequence number to be expected by the sender when the ACK control bit is set. (32 bits)
- Data Offset / Header Length Field works with the other fields because it indicates how many 32-bit options are contained in the TCP header. It’s important to note the header length and options field have variable length. (variable length)
- Reserved field - These bits are always set to zero and comes into play for future use (6 bits)
- Flags: (6bits) URG—flags that some urgent data has been placed. ACK—flags the acknowledgement number is valid. PSH—flags that data should be passed to the application as soon as possible. RST—Resets the connection. SYN—Synchronizes sequence numbers to initiate a connection. FIN—Means that the sender of the flag has finished sending data. Note: recognize a couple of these flags for the three way handshake ;P
- Window field explains how much space is available for incoming data on the side of the sender (16 bits)
- Checksum Field verifies the integrity of the header, if it’s damaged or has been altered in transit (16 bits)
- Urgent pointer field indicates the first urgent data byte in the packet
- Options field allows for various TCP options to be leveraged, one prime example of this is during the 3 way handshake you can see the MSS(Maximum Segment Size) option being used to determine MSS for the transmissions (Variable Multiple of 8 bits)
- Data field is where the data is from the upper layer protocols using TCP.
As you can tell TCP already has a lot more features as a transport layer protocol than UDP does, which makes it the perfect protocol for most needs, it’s no surprise most TCP/IP protocols are based on TCP, which is based on IP, the model and suite is called TCP/IP afterall :) So let’s wrap things up by breaking down IP.
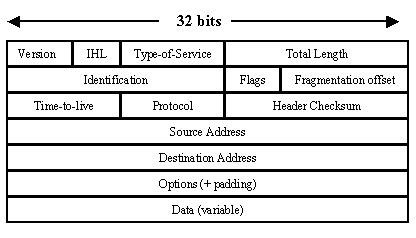
IP: Internet Protocol RFC 791
IP adds an extra header on top of the details attached by TCP or UDP. As you can expect the IP header includes IP addresses, packet length, and packet sequence order. The packet information helps in the instances where the packet exceeds the allowable byte size for network packets and need to be fragmented.
- Version field indicates IPv4 or IPv6 (4 bits)
- IP Header Length indicates how many 32-bit words are in the IP header.(4 bits)
- Type-of-service specifies how the upper-layer protocol wants the packet to be handled. Packets can be assigned various levels of importance here. (8 bits)
- Total Length is the length of the entire IP packet, including data and header, in bytes. (16 bits)
- Identification contains an integer that identifies the current packet should a stream get fragmented and the packet needs to be reconstructed. (16 bits)
- Flags field controls whether the packet is allowed to be fragmented and if so what parts are what for the receiver to put it back together. (4 bits)
- Time-to-live(ttl) keeps packets from looping endlessly by maintaining a counter that decreases to zero, which is when the packet is dropped. (8 bits)
- Protocol field (8 bits) indicates which upper-layer protocol receives incoming packets after IP processing is complete.
- Header Checksum field (16 bits)
- Source Address field (32 bits)
- Destination Address field (32 bits)
- Options field allows IP to support various options, such as security. (32 bits)
- Data field (32 bits)