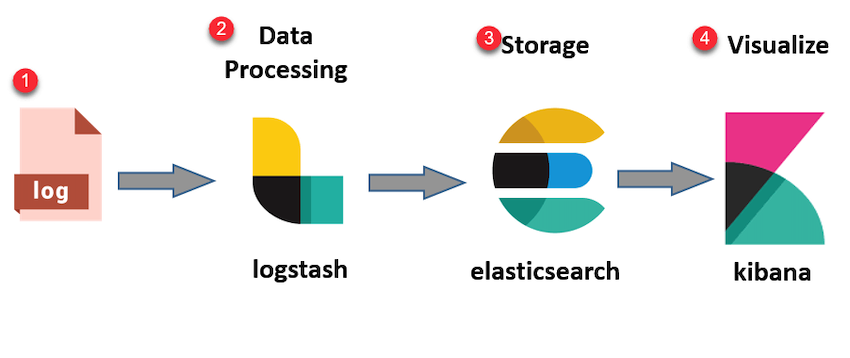
How To Install Elastic Stack (ELK) on CentOS 8
Hey Folks!
Today I’m gonna walk y’all through the process of installing the ELK Stack on a CentOS 8 Host.
Prerequisites
Install Java 8+
sudo dnf install java-1.8.0-openjdk
Installing The Elastic Repositories
sudo rpm ––import https://artifacts.elastic.co/GPG-KEY-elasticsearch
cd /etc/yum.repos.d/
...

Find and Lead the Perfect Remote Team With These Simple Tips
This Article Has Been Written By Tina Martin of Ideaspired Check Her Out!
With so many changes occurring in the business world these days due to Covid-19, it’s no surprise that many companies are choosing to allow their employees to work from home. Remote employees and businesses alike have seen multiple benefits from this break from the norm, ...

The Jester's Castle Episode 3
Hello Friends!
ACT Has 6 Core Processes in what is lightheartedly called The Act Hexaflex:
Contact with the present moment: Be Here Now
Defusion: watch your thinking
I’m Acceptance: open up
Self-as-context: the noticing self
Values: know what matters
Committed Action: do what it takes
Contact with the Present Moment
...

The Jester's Castle Episode 2
Hello Friends!
/center>
Today we’re gonna talk about the supply chain, and more specifically supply chain attacks.
The software supply chain is vulnerable, and every vendor is vulnerable so everyone must do their due diligence.
The supply chain is such a hard element to secure because it spreads cross company which means when choosing who...

SANS Holiday Hack Challenge 2020 Write-Up Part 2/2
Hey Everyone! Glad You're Still Here Cracking At The SANS Holiday Hack Challenge AKA KRINGLE CON 3 (2020)!
If y’all missed part one you can just reverse reverse! Clicking here : https://www.jameskainth.com/cyber/2021/01/11/HolidayHackChallenge2020.html
At this point we’re 2 almost 3 Christmas trees in, so the challenges aren’t necessarily craz...

SANS Holiday Hack Challenge 2020 Write-Up Part 1/2
Hey Everyone! Today I wanted to go over the latest SANS Holiday Hack Challenge AKA KRINGLE CON 3 (2020)!
So fair warning, I wasn’t able to complete the whole challenge but I did get a lot further than I initially thought I would and that’s why I’m feeling groovy enough to publish this 😜. So let’s dig in and recap what was a super fun event and ...

Graduating & Starting Work During The COVID-19 Global Pandemic
Disclaimer: I must inform readers that the views, thoughts, and opinions expressed in this text belong solely to me James Kainth, and not necessarily to my employer, organization, committee or any other group or individual.
Lol Yes, That is New. Look at me I’m cool I get to put that disclaimer on some of my posts now 😉 Did I necessarily need to...

Let's Talk: ZAT
What Is ZAT?
The Full Code Can Be Found Here: https://github.com/SuperCowPowers/zat/blob/master/examples/anomaly_detection.py Full credit to SuperCowPowers and the team there. They’re a very cool group that’s flying under the radar of many.
I’m gonna showcase some excerpts of their code for those who are unfamiliar and would like to know wh...
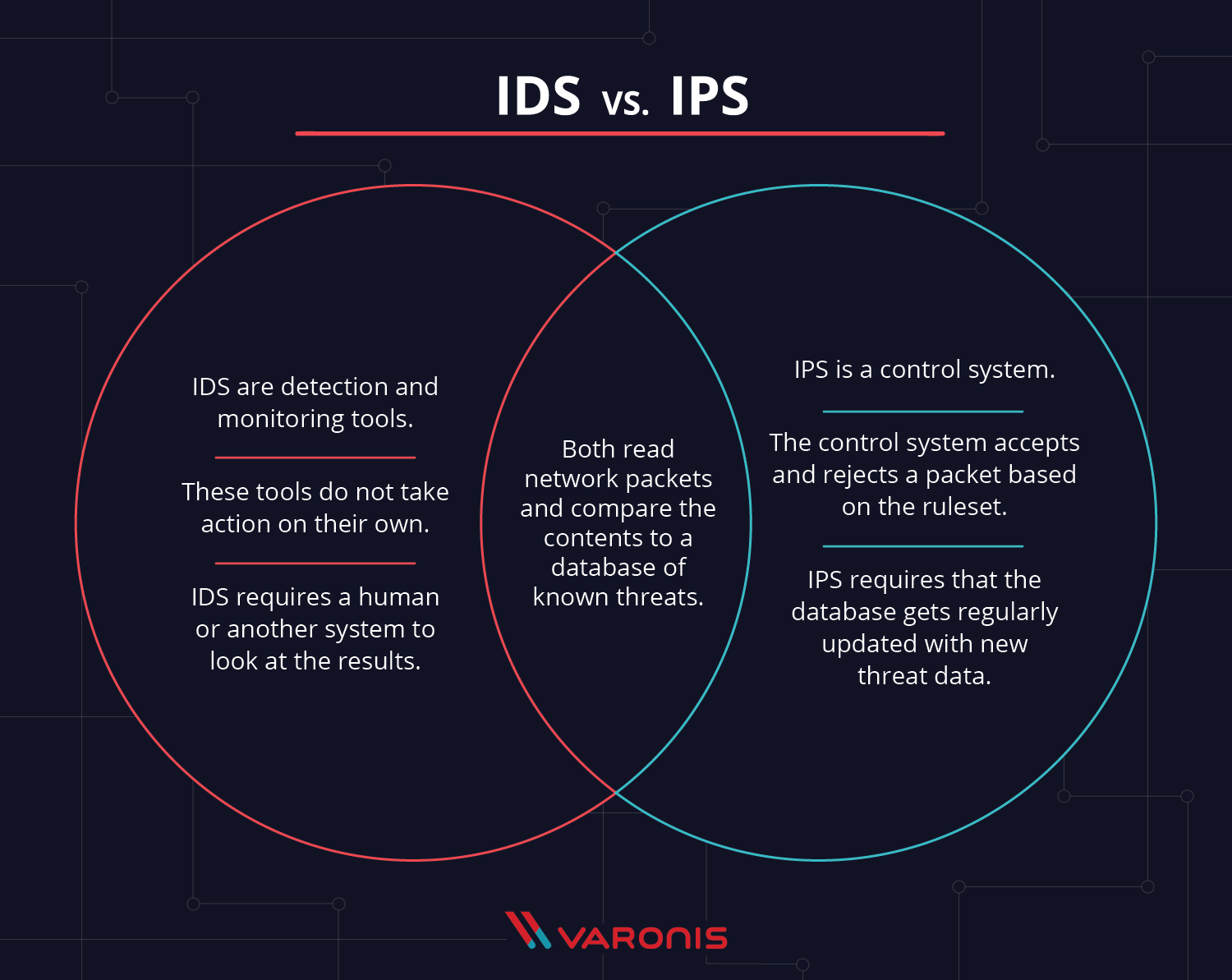
Let's Talk: IDS(Intrusion Detection Systems)
Hi Everyone!
This is the first post I’ve been making in relation to my capstone! My capstone utilizes Zeek logs partnered with some python tools that leverage machine learning algorithms for anomaly detection and also visualizations! Today, let’s talk about Zeek! Well, what’s Zeek? Zeek, is actually the world’s leading network security monitori...

Let's Talk: Ubuntu 20 ‐ WireGuard Kernel Protocol
Howdy folks!
If you’ve read some of my latest blog posts, you’ll notice that I’ve been hopping over to the updated versions of my virtual machines latest operating systems, respectively. Last Ubuntu machine I used was Ubuntu 19, but to my surprise a mere three days later Ubuntu 20 was released! Focal Fossa as it is aptly named!
There’s a lot o...

Quick Chat: Shadowsocks
Howdy howdy peeps!
Today I just wanted to really quickly chat about a software I recently tested out for the fun of it that’s frequently used over in China! So I know using a proxy isn’t the best when you can use a VPN but, lol. Let’s forget about that for the sake of the chat here.
Let’s Have a Quick Chat!
Shadowsocks is a Secure Socks5 Prox...
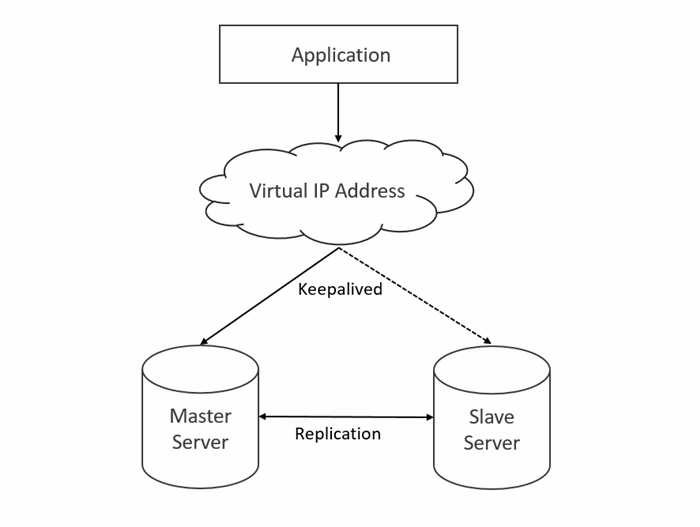
Quick Chat: Keepalived
Howdy Peeps! Time for another Quick Chat! This time I wanna give a real quick attention burst over to Keepalived. So for those of you that are familiar with VRRP from our previous quick chat on it you are mainly familiar with implementing VRRP on VyOS firewalls. Now what if you wanted to have a virtual ip between two different servers, and you d...

Quick Chat: Server Load Balancing and Redundancy with HA Proxy
What is HA Proxy?
HA Proxy is a free and open source load balancer and proxy server for tcp and HTTP based applications that allows for spread requests across multiple servers.
How To Install HA Proxy? (For This Chat I’m on Ubuntu 18.04):
sudo add-apt-repository ppa:vbernat/haproxy-1.8
sudo apt-get update
sudo apt-get install haproxy
...
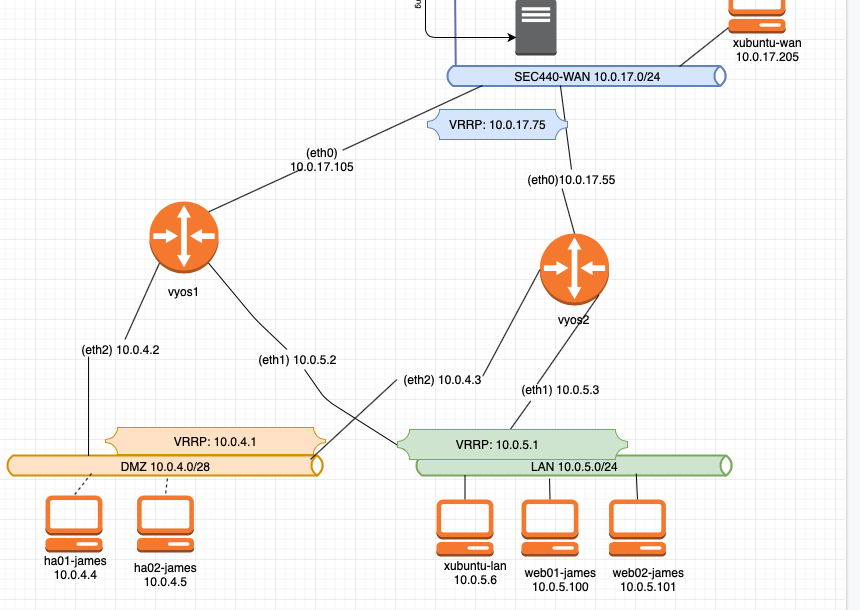
Quick Chat: VRRP & MFA
Hey peeps! So it’s my final semester now here at college and I have my final major class. Systems Security aka SEC440. It’s a no nonsense, no handholding, no spoon feeding class where you’re given tasks that you have no idea how to do, and you have to go research and figure it out. Honestly, I hate it and love at the same time. Shoutout to the...
Let's Talk About Metasploit
Wuddup peeps! It’s James here. Last time we went into some extremely rudimentary password cracking for haxoring into a system. This week let’s get into one of the essential skid toolz to have in your arsenal as an elite “hacker”…I mean Cyber Security Student… 😛 Lol I am now forced to say James does not condone black hat hacking as defined by hur...

Let's Talk About: Password Cracking
Wuddup everyone it’s ya boi James here. So you know how my teacher wanted me to write that tech journal assignment. Well I figured ya know what James why don’t we fight back 😉 So I figured why not make my lab assignments my tech journal, and why don’t I make my blog posts my tech journals. So ya boi kills three birds with one stone 🙂 🙂 (James do...
Quick Chat: Nmap, fping, TheHarvester, Nessus, OpenVAS
What’s up folks! So my teacher wants me to write about some of the tools we’ve used in class. Yea no joke. I know I didn’t post last week, I’ve been busy the standard excuse. But I’m gonna start making some videos for y’all about networking this weekend. You know like Active Directory, DNS, etc. So stay tuned! But for know I gotta get this homew...
Let's Talk About Pentesting
Hey folks!
So now you’ve learned a little bit about incident response but now you’re like well thanks James, but what goes through an attackers mindset? That gets us to Penetration Testing!! Uhhhh what? Penetration Testing…What does that mean James? I know I know without context of the cybers you’re confused, it’s ok. Low brow jokes aside, Pen ...

Let's Talk About Incident Response
Hey folks,
So a lot of you have been asking me about incident response(IR). What is it? How does it work? How does it relate to Cyber Security? So I’m making this post to talk about IR in a very rudimentary way without going into a very big technical deep dive.
What is Incident Response?
Incident Response is basically an organized approach to ...

What To Do On The First Week Of Classes
It’s often that when you come into college you get really excited to take a course and you’re ready to, let’s say learn HTML/CSS and then half way through the semester you realize that you’re not learning at all! You’re just sitting on your computer and your professor has you going through rudimentary Code Academy tutorials and flipping through ...