The OSI and TCP/IP Model - Networking Basics - Part 5
Wuddup Everyone! It’s your boi Jester James here coming at you with another youtube video, today I’m going to be talking about the OSI Model and The TCP /IP Model. Both of which are conceptual frameworks used to describe the functions of networking systems…basically the OSI and TCP/IP models are tools we can add to our NetAdmin tool belt to remind us of important tips for troubleshooting.
They Break Down what’s going on at different levels of problems in computers, going from the physical level with hardware to the application level with software programs. If you’ve watched my previous videos in the Networking Basics series you’ll recognize some of what we cover today, for example, you’ll recognize protocols.
So Think of the layers of these models as different lenses you can use to focus on things when troubleshooting. It allows you to zoom in and out of the hardware, technical, and software layers of computer networking.
So Let’s Get Started By Learning The OSI MODEL !
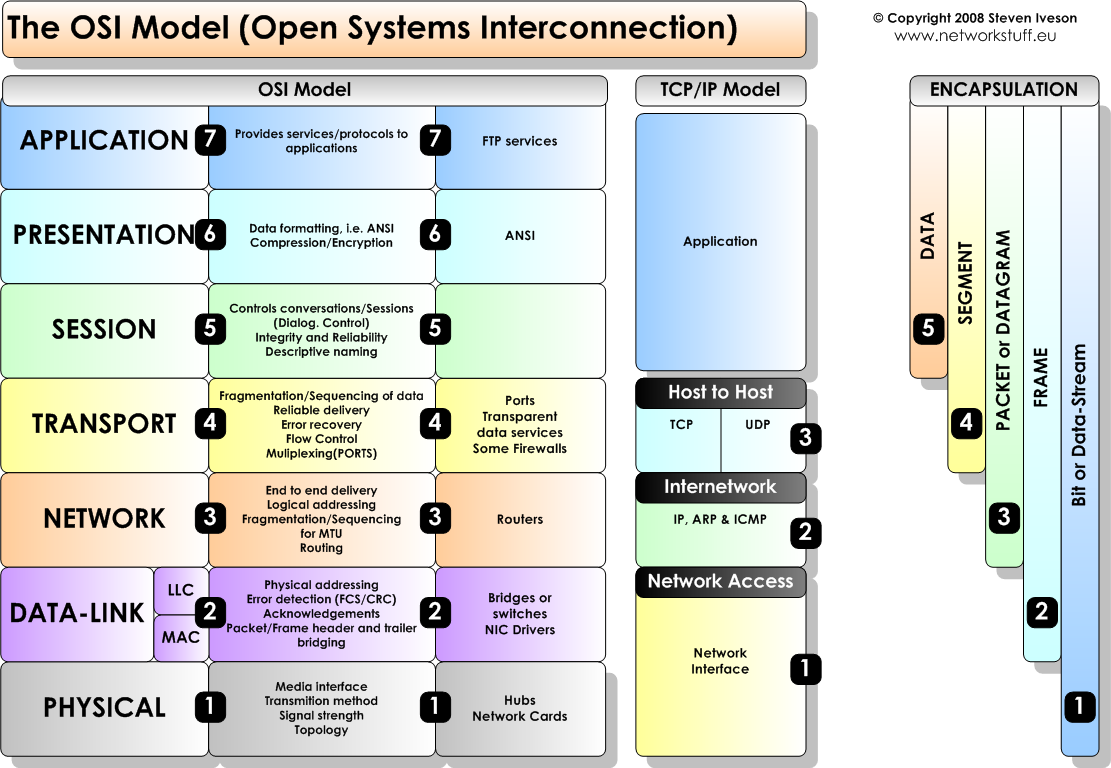
Layer 1: Physical Layer The physical layer defines the electrical and physical specifications of the data connection. For example, the layout of pins of the connector, like the rj45 ethernet connector, or the frequency for wireless devices like 2 or 5Ghz on routers you’ll find; The 2.4 GHz band provides coverage at a longer range but transmits data at slower speeds. The 5 GHz band provides less coverage but transmits data at faster speeds. You see it’s bound to the physical layer, because it is responsible for transmission and reception of unstructured raw data in a physical medium. Bit rate control is done at the physical layer. It is the layer of low-level networking equipment and is never concerned with protocols or other higher-layer items. Which leads us to Layer 2.
Layer 2: Data Link Layer The data link layer takes a look at the node-to-node connectivity or link between two directly connected nodes. It handles packaging and unpacking the data in frames; raw network packets are unpacked network data frames. You can see this more clearly in the MAC protocol to work with ARP which is a Layer 3 Network protocol to give these nodes or devices addresses to connect to one another. The Data Link Layer, however, defines the protocol to establish and terminate a connection between two physically connected devices. The data link layer is generally divided into two sublayers—media access control (MAC) layer and logical link control (LLC) layer. The LLC layer is responsible for identifying and encapsulating network layer protocols, and controls error checking and frame synchronization. The MAC layer is responsible for controlling how devices in a network gain access to a media and permission to transmit data. Think of the MAC protocol linking MAC Addresses and IP addresses. The IP address handling of the MAC protocol then bridges us into the Network Layer using the ARP protocol to resolve MAC addresses with IP addresses so remember that ARP(the Address Resolution Protocol) and the IP protocol is on Layer 3 of the OSI Model, The Network Layer.
Layer 3: Network Layer The network layer handles packet routing via logical addressing and switching functions. A network is a medium to which many nodes can be connected. Every node has an address. When a node needs to transfer a message to other nodes, it can merely provide the content of the message and the address of the destination node, then the network will find the way to deliver the message to the destination node, possibly routing through other nodes. If the message is too long, the network may split it into several segments at one node, sending them separately and reassembling the fragments at another node. The IP, ICMP, OSPF, and ARP protocols all operate on Layer 3 of the OSI Model
Layer 4: Transport Layer The transport layer provides the functions and means of transferring data sequences from a source to a destination host via one or more networks, while maintaining the quality of service (QoS) functions and ensuring the complete delivery of the data. The integrity of the data can be guaranteed via error correction and similar functions. It can also provide an explicit flow control function. Though not strictly conforming to the OSI model, the TCP and User Datagram Protocols (UDP) are essential protocols in layer 4.
Layer 5: Session Layer The session layer controls the dialogues (connections) between computers. It establishes, manages, maintains and ultimately terminates the connections between the local and remote application. Layer 5 software also handles authentication and authorization functions. It verifies the data is delivered as well. The session layer is commonly implemented explicitly in application environments that use remote procedure calls.
Layer 6: Presentation Layer The presentation layer checks the data to ensure it is compatible with the communications resources. It translates the data into the form that the application level and lower levels accept. Any needed data formatting or code conversion is also handled by the sixth layer, such as the American Standard Code for Information Interchange (ASCII) code for text files. It functions for data compression and encryption as well. For example, video calls will be compressed during the transmission so that it can be transmitted faster, and the data will be recovered at the receiving side. For the data that has high security requirements, such as a text message containing your password, it will be encrypted at this layer.
Layer 7: Application Layer The application layer of the OSI model interacts directly with software applications to provide communication functions as required, and it is the closest to end users. Functions of the application layer typically include verifying the availability of communication partners and resources to support any data transfer. This layer also defines protocols for end applications, such as domain name system (DNS), file transfer protocol (FTP), hypertext transfer protocol (HTTP), Internet message access protocol (IMAP), post office protocol (POP), simple mail transfer protocol (SMTP), Simple Network Management Protocol (SNMP), and Telnet (a terminal emulation).
TCP/IP
Network Access Layer Network access layer (or link layer) is responsible for placing the TCP/IP packets on the network medium and receiving TCP/IP packets off the network medium. TCP/IP is designed to be independent of the network access method, frame format, and medium. It is independent from any specific network technology. In this way, TCP/IP can be used to connect different network types, such as Ethernet, Token Ring, and Frame Relay.
Internet Layer The Internet layer is responsible for host addressing, packaging, and routing functions. The core protocols of the Internet protocol layer are IP, Address Resolution Protocol (ARP), Internet Control Message Protocol (ICMP) and Internet Group Management Protocol (IGMP). The IP is a routable protocol responsible for IP addressing, routing, and the fragmentation and reassembly of packets. The ARP is responsible for discovering the network access layer address, such as a hardware address associated with a given Internet layer access. The ICMP is responsible for providing diagnostic functions and reporting errors due to the unsuccessful delivery of IP packets. The IGMP is responsible for the management of IP multicast groups. In this layer, the IP adds a header to the packets, which is the IP address. Now there’s both IPv4 (32-bit) address and IP Ipv6 (128-bit) address.
Transport Layer The transport layer, also known as the host-to-host transport layer, is responsible for providing the application layer with session and datagram communication services. The core protocols of this layer are TCP and UDP. TCP provides a one-to-one, connection-oriented, reliable communications service. It is responsible for sequencing and acknowledgment of packets sent, and recovery of packets lost in transmission. UDP provides one-to-one or one-to-many, connectionless, unreliable communications services. UDP is used typically when the amount of data to be transferred is small (such as that data would fit into a single packet).
Application Layer The application layer of the TCP/IP model provides applications the ability to access the services of the other layers, and defines the protocols that applications use to exchange data. Most widely-known application layer protocols include HTTP, FTP, SMTP, Telnet, DNS, SNMP and Routing Information Protocol (RIP).